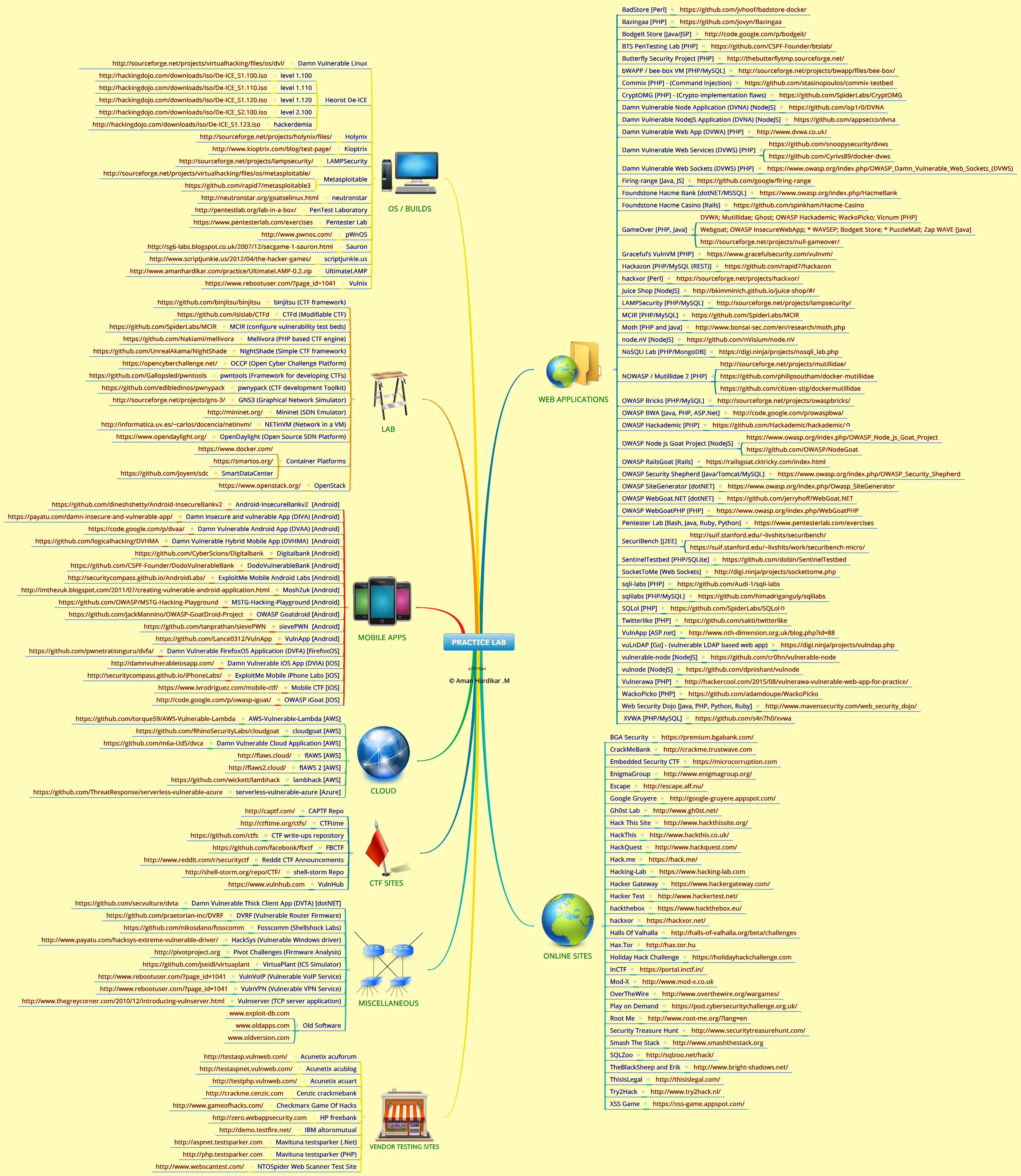
| Aplicativos da Web vulneráveis |
| BadStore | http://www.badstore.net/ |
| BodgeIt Store | http://code.google.com/p/bodgeit/ |
| Projeto de segurança da borboleta | http://thebutterflytmp.sourceforge.net/ |
| bWAPP | http://www.mmeit.be/bwapp/
http://sourceforge.net/projects/bwapp/files/bee-box/ |
| Commix | https://github.com/stasinopoulos/commix-testbed |
| CryptOMG | https://github.com/SpiderLabs/CryptOMG |
| Aplicativo de nó vulnerável (DVNA) | https://github.com/quantumfoam/DVNA/ |
| Maldito aplicativo da Web vulnerável (DVWA) | http://www.dvwa.co.uk/ |
| Serviços Web Vulneráveis (DVWS) | http://dvws.professionallyevil.com/ |
| Bêbado Admin Web Hacking Challenge | https://bechtsoudis.com/work-stuff/challenges/drunk-admin-web-hacking-challenge/ |
| Explorar o aplicativo da Web vulnerável da KB | http://exploit.co.il/projects/vuln-web-app/ |
| Foundstone Hackme Bank | http://www.mcafee.com/us/downloads/free-tools/hacme-bank.aspx |
| Foundstone Hackme Books | http://www.mcafee.com/us/downloads/free-tools/hacmebooks.aspx |
| Foundstone Hackme Casino | http://www.mcafee.com/us/downloads/free-tools/hacme-casino.aspx |
| Foundstone Hackme Shipping | http://www.mcafee.com/us/downloads/free-tools/hacmeshipping.aspx |
| Viagem para Foundstone Hackme | http://www.mcafee.com/us/downloads/free-tools/hacmetravel.aspx |
| Fim de jogo | http://sourceforge.net/projects/null-gameover/ |
| hackxor | http://hackxor.sourceforge.net/cgi-bin/index.pl |
| Hackazon | https://github.com/rapid7/hackazon |
| LAMPSecurity | http://sourceforge.net/projects/lampsecurity/ |
| Traça | http://www.bonsai-sec.com/en/research/moth.php |
| NOWASP / Mutillidae 2 | http://sourceforge.net/projects/mutillidae/ |
| OWASP BWA | http://code.google.com/p/owaspbwa/ |
| OWASP Hackademic | http://hackademic1.teilar.gr/ |
| OWASP SiteGenerator | https://www.owasp.org/index.php/Owasp_SiteGenerator |
| Tijolos OWASP | http://sourceforge.net/projects/owaspbricks/ |
| Pastor de Segurança da OWASP | https://www.owasp.org/index.php/OWASP_Security_Shepherd |
| PentesterLab | https://pentesterlab.com/ |
| PHDays iBank CTF | http://blog.phdays.com/2012/05/once-again-about-remote-banking.html |
| SecuriBench | http://suif.stanford.edu/~livshits/securibench/ |
| SentinelTestbed | https://github.com/dobin/SentinelTestbed |
| SocketToMe | http://digi.ninja/projects/sockettome.php |
| sqli-labs | https://github.com/Audi-1/sqli-labs |
| MCIR (arco-íris de injeção de código mágico) | https://github.com/SpiderLabs/MCIR |
| sqlilabs | https://github.com/himadriganguly/sqlilabs |
| VulnApp | http://www.nth-dimension.org.uk/blog.php?id=88 |
| PuzzleMall | http://code.google.com/p/puzzlemall/ |
| WackoPicko | https://github.com/adamdoupe/WackoPicko |
| WAED | http://www.waed.info |
| WebGoat.NET | https://github.com/jerryhoff/WebGoat.NET/ |
| Dojo do WebSecurity | http://www.mavensecurity.com/web_security_dojo/ |
| XVWA | https://github.com/s4n7h0/xvwa |
| Zap WAVE | http://code.google.com/p/zaproxy/downloads/detail?name=zap-wave-0.1.zip |
| Instalações vulneráveis do sistema operacional |
| 21LTR | http://21ltr.com/scenes/ |
| Maldito Linux vulnerável | http://sourceforge.net/projects/virtualhacking/files/os/dvl/ |
| exercícios de exploração - nebulosa, protostar, fusão | http://exploit-exercises.com/download |
| heorot: DE-ICE, hackerdemia | http://hackingdojo.com/downloads/iso/De-ICE_S1.100.iso
http://hackingdojo.com/downloads/iso/De-ICE_S1.110.iso
http://hackingdojo.com/downloads/iso/ De-ICE_S1.120.iso
http://hackingdojo.com/downloads/iso/De-ICE_S2.100.iso
hackerdemia - http://hackingdojo.com/downloads/iso/De-ICE_S1.123.iso |
| Holynix | http://sourceforge.net/projects/holynix/files/ |
| Kioptrix | http://www.kioptrix.com/blog/ |
| LAMPSecurity | http://sourceforge.net/projects/lampsecurity/ |
| Metaploitable | http://sourceforge.net/projects/virtualhacking/files/os/metasploitable/ |
| Estrêla de Neutróns | http://neutronstar.org/goatselinux.html |
| PenTest Laboratory | http://pentestlab.org/lab-in-a-box/ |
| Pentester Lab | https://www.pentesterlab.com/exercises |
| pWnOS | http://www.pwnos.com/ |
| RebootUser Vulnix | http://www.rebootuser.com/?page_id=1041 |
| Segundo jogo: Sauron | http://sg6-labs.blogspot.co.uk/2007/12/secgame-1-sauron.html |
| scriptjunkie.us | http://www.scriptjunkie.us/2012/04/the-hacker-games/ |
| UltimateLAMP | http://www.amanhardikar.com/mindmaps/practice-links.html |
| TurnKey Linux | http://www.turnkeylinux.org/ |
| Bitnami | https://bitnami.com/stacks |
| Servidor Elástico | http://elasticserver.com |
| Caixas de SO | http://www.osboxes.org |
| VirtualBoxes | http://virtualboxes.org/images/ |
| VirtualBox Virtual Appliances | https://virtualboximages.com/ |
| CentOS | http://www.centos.org/ |
| Clientes Windows padrão | https://www.microsoft.com/en-us/evalcenter/evaluate-windows-10-enterprise
https://dev.windows.com/en-us/microsoft-edge/tools/vms/ |
| Servidor Windows padrão | https://www.microsoft.com/en-us/evalcenter/evaluate-windows-server-technical-preview |
| VMWare vSphere padrão | http://www.vmware.com/products/vsphere/ |
| Sites para baixar versões mais antigas de vários softwares |
| Exploit-DB | http://www.exploit-db.com/ |
| Aplicativos antigos | http://www.oldapps.com/ |
| Versão antiga | http://www.oldversion.com/ |
| VirtualHacking Repo | sourceforge.net/projects/virtualhacking/files/apps%40realworld/ |
| Sites de fornecedores de software de teste de segurança |
| Acunetix acuforum | http://testasp.vulnweb.com/ |
| Acunetix acublog | http://testaspnet.vulnweb.com/ |
| Acunetix acuart | http://testphp.vulnweb.com/ |
| Crackmebank cênico | http://crackme.cenzic.com |
| HP freebank | http://zero.webappsecurity.com |
| IBM altoromutual | http://demo.testfire.net/ |
| Mavituna testsparker | http://aspnet.testsparker.com |
| Mavituna testsparker | http://php.testsparker.com |
| Site de teste do NTOSpider | http://www.webscantest.com/ |
| Sites para melhorar suas habilidades de hackers |
| CTF de segurança incorporada | https://microcorruption.com |
| EnigmaGroup | http://www.enigmagroup.org/ |
| Fuga | http://escape.alf.nu/ |
| Google Gruyere | http://google-gruyere.appspot.com/ |
| Gh0st Lab | http://www.gh0st.net/ |
| Hackear este site | http://www.hackthissite.org/ |
| HackThis | http://www.hackthis.co.uk/ |
| HackQuest | http://www.hackquest.com/ |
| Hack.me | https://hack.me |
| Hacking-Lab | https://www.hacking-lab.com |
| Desafio Hacker | http://www.dareyourmind.net/ |
| Teste de hackers | http://www.hackertest.net/ |
| Jogo hACME | http://www.hacmegame.org/ |
| Halls Of Valhalla | http://halls-of-valhalla.org/beta/challenges |
| Hax.Tor | http://hax.tor.hu/ |
| OverTheWire | http://www.overthewire.org/wargames/ |
| PentestIT | http://www.pentestit.ru/en/ |
| CSC Play on Demand | https://pod.cybersecuritychallenge.org.uk/ |
| pwn0 | https://pwn0.com/home.php |
| RootContest | http://rootcontest.com/ |
| Root Me | http://www.root-me.org/?lang=en |
| Caça ao tesouro de segurança | http://www.securitytreasurehunt.com/ |
| Smash The Stack | http://www.smashthestack.org/ |
| SQLZoo | http://sqlzoo.net/hack/ |
| TheBlackSheep e Erik | http://www.bright-shadows.net/ |
| ThisIsLegal | http://thisislegal.com/ |
| Try2Hack | http://www.try2hack.nl/ |
| WabLab | http://www.wablab.com/hackme |
| XSS: você pode XSS isso? | http://canyouxssthis.com/HTMLSanitizer/ |
| XSS Game | https://xss-game.appspot.com/ |
| XSS: ProgPHP | http://xss.progphp.com/ |
| Sites / Arquivos da CTF |
| Repositório CAPTF | http://captf.com/ |
| CTFtime (detalhes dos desafios do CTF) | http://ctftime.org/ctfs/ |
| Repositório de registros do CTF | https://github.com/ctfs |
| Anúncios do Reddit CTF | http://www.reddit.com/r/securityctf |
| Repo | http://shell-storm.org/repo/CTF/ |
| VulnHub | https://www.vulnhub.com |
| Aplicativos móveis |
| Maldito aplicativo Android vulnerável (DVAA) | https://code.google.com/p/dvaa/ |
| Maldito aplicativo FirefoxOS vulnerável (DVFA) | https://github.com/pwnetrationguru/dvfa/ |
| Maldito aplicativo iOS vulnerável (DVIA) | http://damnvulnerableiosapp.com/ |
| ExploitMe Mobile Android Labs | http://securitycompass.github.io/AndroidLabs/ |
| Laboratórios para iPhone do ExploitMe Mobile | http://securitycompass.github.io/iPhoneLabs/ |
| Hacme Bank Android | http://www.mcafee.com/us/downloads/free-tools/hacme-bank-android.aspx |
| InsecureBank | http://www.paladion.net/downloadapp.html |
| NcN Wargame | http://noconname.org/evento/wargame/ |
| OWASP iGoat | http://code.google.com/p/owasp-igoat/ |
| OWASP Goatdroid | https://github.com/jackMannino/OWASP-GoatDroid-Project |
| Lab |
| binjitsu | https://github.com/binjitsu/binjitsu |
| CTFd | https://github.com/isislab/CTFd |
| Mellivora | https://github.com/Nakiami/mellivora |
| NightShade | https://github.com/UnrealAkama/NightShade |
| MCIR | https://github.com/SpiderLabs/MCIR |
| Docker | https://www.docker.com/ |
| Vagabundo | https://www.vagrantup.com/ |
| NETinVM | http://informatica.uv.es/~carlos/docencia/netinvm/ |
| SmartOS | https://smartos.org/ |
| SmartDataCenter | https://github.com/joyent/sdc |
| Hypervisor do vSphere | https://www.vmware.com/products/vsphere-hypervisor/ |
| GNS3 | http://sourceforge.net/projects/gns-3/ |
| OCCP | https://opencyberchallenge.net/ |
| XAMPP | https://www.apachefriends.org/index.html |
| Diversos |
| VulnVPN | http://www.rebootuser.com/?page_id=1041 |
| VulnVoIP | http://www.rebootuser.com/?page_id=1041 |
| Vulnserver | http://www.thegreycorner.com/2010/12/introducing-vulnserver.html |
| NETinVM | http://informatica.uv.es/~carlos/docencia/netinvm/ |
| DVRF | https://github.com/praetorian-inc/DVRF |
| Driver Vulnerável ao HackSys Extreme | http://www.payatu.com/hacksys-extreme-vulnerable-driver/ |
| VirtuaPlant | https://github.com/jseidl/virtuaplant |
| Fosscomm | https://github.com/nikosdano/fosscomm |
| Captura da manhã | http://blog.cobaltstrike.com/2014/08/06/introducing-morning-catch-a-phishing-paradise/ |
| AWBO | https://labs.snort.org/awbo/awbo.html |







Comentários
Postar um comentário