Compartilhe
- Gerar link
- X
- Outros aplicativos
Tools for forensics
Tools for forensics and combating it
Good afternoon, my Bunnies in hats🎩🐰
Let's go drink tea?🫖

While I was writing an article about mobile forensics (which is in the final stages of writing), I decided to make a small selection of tools for conventional forensics and anti-forensics.
Hope you enjoy ❤️
Anticriminology is a method of combating forensic science.
In a word: make it so that they cannot find you, and if they could, they would not be able to prove that they found you.
This collection contains tools primarily for PC, not for mobile devices.
Surprisingly-anti-judicial
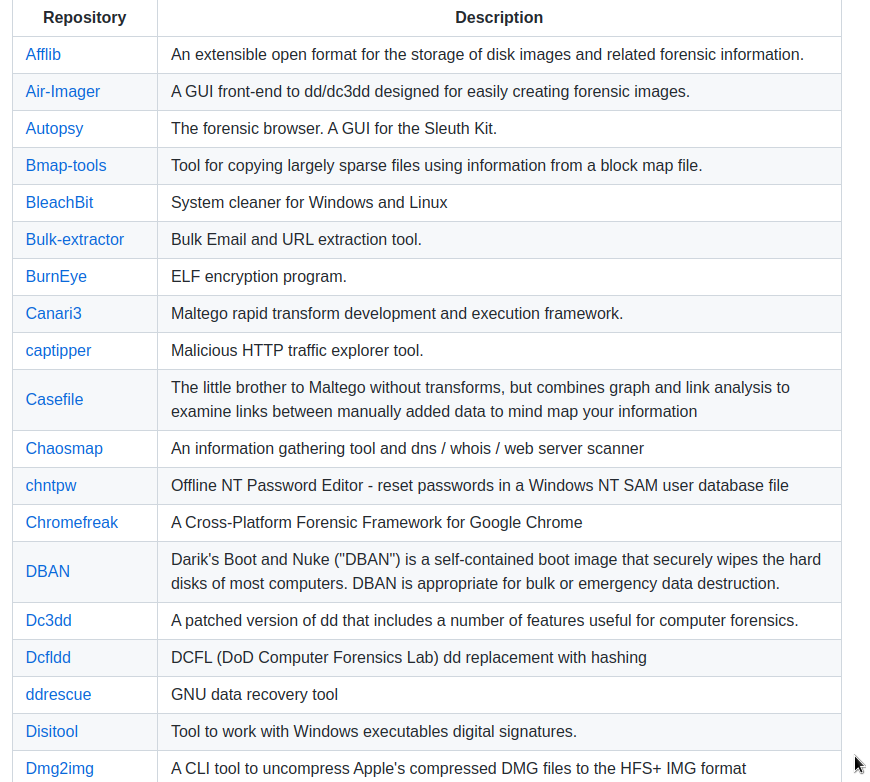
Tools and packages used for anti-forensics and forensics, including encryption, steganography, and anything that changes attributes.
There are funds for:
storage of disk images;
A browser designed to protect against forensics;
Tools for copying sparse files using information from a block map file;
various cleaning products;
ELF encryption tools
Also GNU data recovery tools for forensics;
A set of tools for checking NTFS artifacts;
facebook memory forensic utility;
Tools for parsing PDF documents;
Tool for detecting steganographic content in images;
Unix tool for secure removal;
And even decoders;
I think it will be very interesting to meet you.
WinLogs-Killer
This tool can clear various logs and history files saved by Windows. 🪟
Now he can remove:
Windows event logs
History of Windows Remote Desktop;
Recent Windows Files
Appear
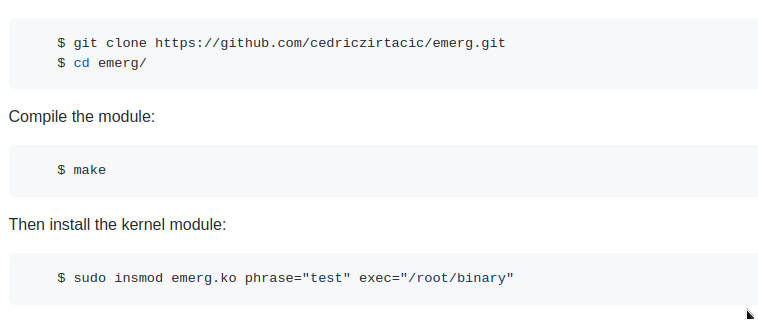
lkm module for emergency launch of binaries/scripts
It will always run in the background (from kernel space), and when you enter the "secret" passphrase, it will do whatever was specified.
This works with standard terminals (tty), not pseudo terminals (pty).
The module has two parameters, one for the phrase (be careful with this) and the second will be the path to the executable.
Phrase : Entering this phrase will be the trigger, so choose wisely
Exec : executable file (This can be a binary file or a script.)
Kaiser
An interesting virus of its qualities:
Fileless persistence, attacks and anti-forensic capabilities.
This project is NOT designed to evade AV detection.
One of the most beneficial attributes of malware is survivability as a means of maintaining resilience and evading detection by security solutions.
Since the development of full-fledged malware requires expensive resources, this feature is becoming increasingly desirable in order to remain unknown and undetected at all times.
The nature of such malware should include anti-forensic capabilities in its suite to keep its footprint minimal, as well as tampering with systemic and forensic evidence to prevent it from being captured and analyzed.
Combined with fileless methods, sophisticated malware can be able to attack a system while remaining evasive, avoiding the traditional detection methods developed and refined over the years.
The Kaiser proof-of-concept malware was designed to demonstrate a subset of anti-forensic and fileless features. Such features include fileless saving and binary execution, as well as anti-forensic countermeasures that disable the event logging service and actively prevent the infected machine and itself from being forensically analyzed to prevent any further intrusion investigation.
Anti Forensics
Anti-forensics is the art of leaving no traces on your computer, it fights against common forensic tools by preventing anyone from infiltrating your computer for forensic tests.
This is a good article about the definition and proper tuning of forensic protection methods.
Basic things are told there, but there is a funny presentation and good thoughts slip through.
I think this is worth reading.
Metadata Remover
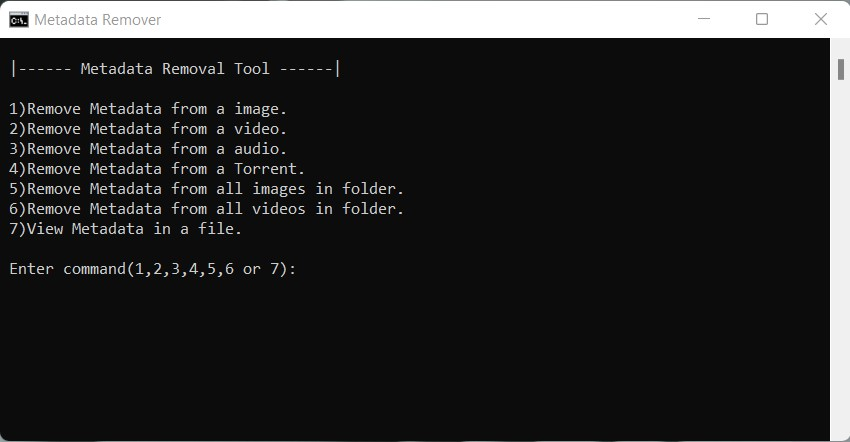
Nowadays it is difficult to get privacy.
Removing unwanted metadata improves privacy. The reduced size of images and videos will be a boon for web developers when embedding images and videos in websites.
This is a simple tool to remove metadata for images and videos using exiftool and ffmpeg in C and Python3.
The Python version of the metadata remover supports audio and torrent files.
This tool does not support any other formats, however, you can use the Document Inspector in Microsoft Office for documents such as docx, pptx, etc.
Fishy
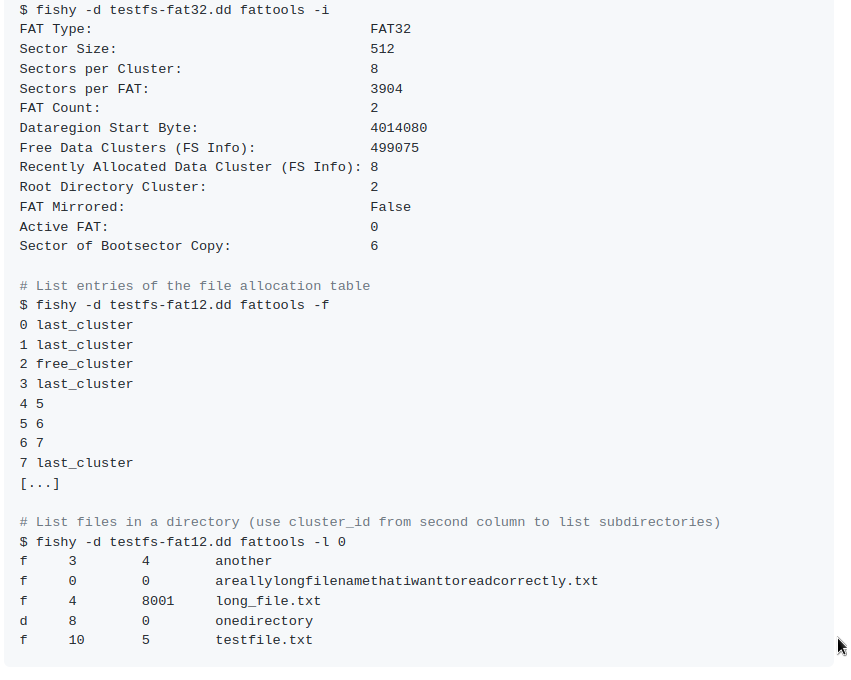
fishy is a toolkit for filesystem-based data hiding methods implemented in Python.
It collects various common exploits that use existing data structures at the file system level to hide data from common file access methods.
This toolkit is designed to educate people about the concept of established anti-forensic techniques related to data hiding.
One of the design goals for fishy was to maintain a modular structure. Separate layers allow functions to be encapsulated. The logical procedure for using fishy is as follows:
The CLI (Command Line Interface) evaluates the options entered by the user and invokes the appropriate hide technique wrapper, which checks the filesystem type and invokes the appropriate hide technique.
If the hide method calls its write method, it will write a json file to disk containing the metadata used to restore the hidden data.
Command line argument parsing is implemented in cli.py, and the hide method wrapper is in the root module. They convert the input data to streams, convert/read/write the metadata of a specific hide method, and call the appropriate methods associated with the selected hide method.
Detection of the filesystem type of a particular image occurs through a wrapper hiding technique that calls filesystem_detector.
The filesystem_detector uses the file system detection methods implemented in the file system modules. The filesystem-specific hiding methods provide the actual functionality and provide at a minimum read, write, and flush methods for reading, hiding, or deleting data.
In addition, hiding methods use pytsk3 or special file system analyzers (which are found in a specific file system package) to collect information about a given file system.
Forensia
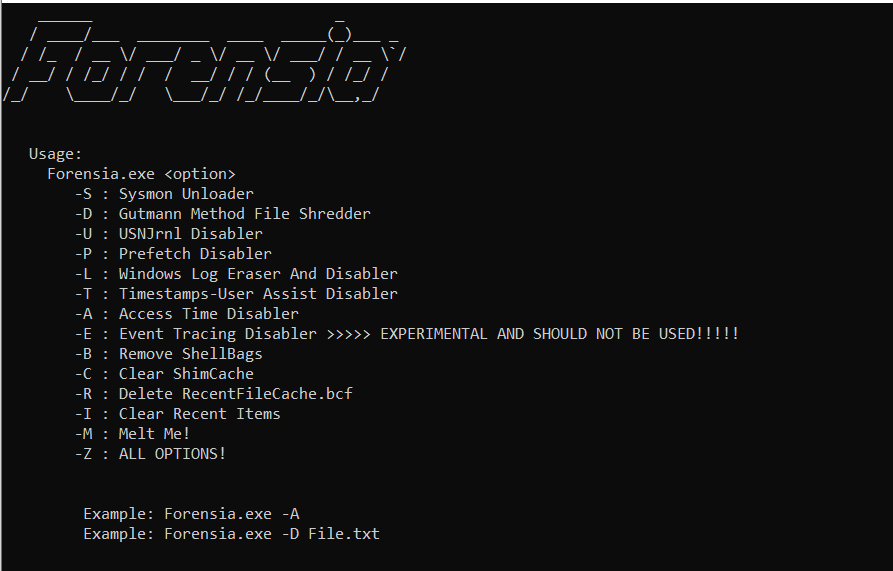
An anti-forensics tool for Red Teamers, used to erase some traces in the post-exploitation phase.
Reduces payload burn-in and increases detection countdown. Can be used to test the capabilities of your Incident Response/Forensic Teams.
Possibilities
Unloading the Sysmon driver.
Shredding files according to the Gutman method.
Disabling USNJrnl.
Disable prefetch.
Tool to remove the log and disable the event log.
User Assist Update Time Disabler.
Disable Access Time.
Delete recent items
Clear shim cache
Clear Recent FileCache
Clear Shell Bag
Remove Windows Defender Quarantine Files
Ability to melt files.
Myool
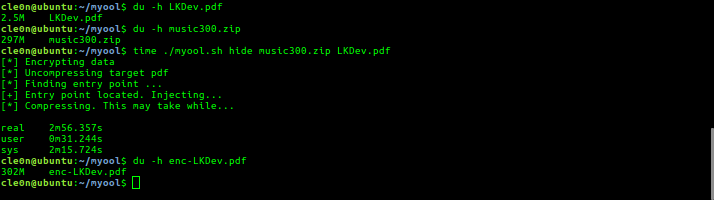
Forensic protection, steganography, data exfiltration. Encrypt the file and hide it in any PDF file.
Python version of myool for Windows and Linux. It's much faster as it doesn't hit the disk multiple times. While functional (not quite), it's not fully done yet. See pymyool.py for the TODO list and usage.
Object options: "/Subtype /Type1C", "/Subtype /Image" or "/BitsPerSample" define streams that can contain raw binary data.
Myool looks for these parameters and their corresponding "end streams" which are written to an array of entry points. Entry points are shuffled randomly and then repeated, copying data chunks to each. Fragments are preceded by a secret key and a sequence number for ease of retrieval. The file signature of the encrypted data is also overwritten, so any attempt to find it will fail unless the secret key is known and the fragments are recovered and reordered.
Awesome-memory-forensics
A curated list of remarkable forensic memory studies for DFIR.
Memory forensics is the forensic analysis of a computer's memory dump. Its primary use is to investigate complex computer attacks that are stealthy enough not to leave data on a computer's hard drive. Therefore, memory (RAM) must be analyzed for forensic information.
Anti-forensic technologies
Cool article with an overview of anti-forensics methods and how they work.
It affects changing timestamps, usnjrnl, changing metadata in the log system.
Anti forensics on usb and much more.
I advise you to read
Anti Forensics
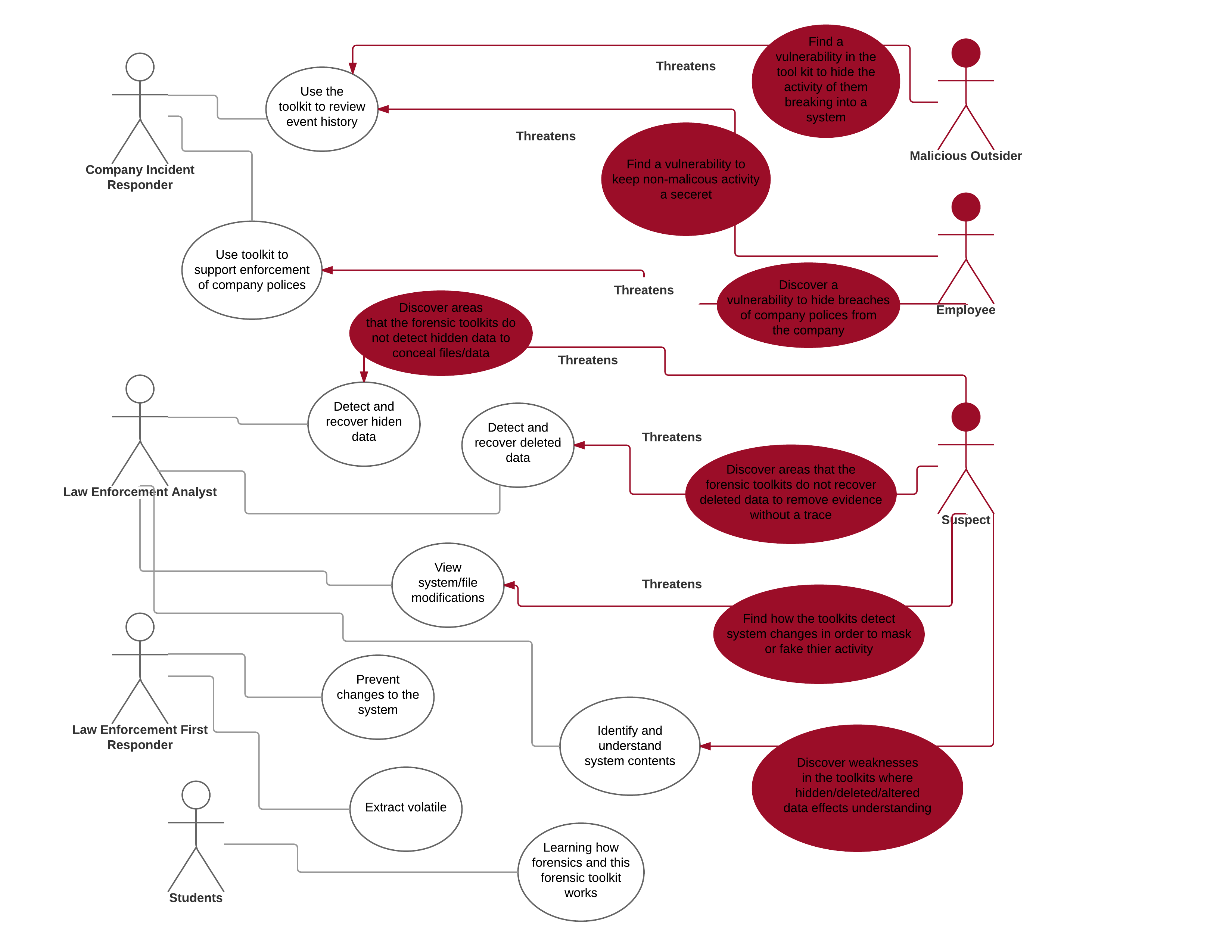
A report showing the strengths and weaknesses of commonly used forensic toolkits.
The study is divided into the following sections:
A study of anti-forensics tools to hide, alter, and destroy data, popular all-in-one forensic toolkits, and a study of documentation strategies to evaluate these forensic toolkits.
Awesome-forensics-1
Awesome Forensics Resources:
Nearly 300 open source forensic tools and 600 forensic blog posts.
Lockwatcher

Anti-forensic monitoring software: Looks for signs of unauthorized access and clears keys/turns everything off.
Lockwatcher is built on the assumption that if someone tries to use your computer when it's locked, they're trying to get your real-time data, so that data needs to be destroyed and the computer made inaccessible.
How the blocker works
You lock your computer whenever you are not physically present at it.
Interaction* with a locked computer causes a crash.
Encryption keys are removed from memory and the computer is turned off.
And it's all.

Thanks for reading 🤍
And remember, if Alice eats a magic cake from the table and it becomes larger, then the hurrying rabbit will not notice her. 🥐🐇
Postagens mais visitadas
🇧🇷 Ferramentas OSINT mais usadas por policiais no Brasil
- Gerar link
- X
- Outros aplicativos
OSINT APLICADO À GOVERNANÇA
- Gerar link
- X
- Outros aplicativos
Investigacao defensiva
- Gerar link
- X
- Outros aplicativos










Comentários
Postar um comentário