Compartilhe
- Gerar link
- X
- Outros aplicativos
Hear No Evil: An Introduction to Audio File Analysis for OSINT
Hear No Evil: An Introduction to Audio File Analysis for OSINT

It’s a new year, and that also means new blog posts about all things OSINT and Digital Forensics. In this one, we’re going to dive into something which has been an obsession of mine for as long as I can remember — the art of hiding messages or information in plain sight.
Specifically, we’re going to look at how to detect — and extract information hidden in malicious or corrupted audio files.
📖 What is Steganography
In its simplest form, the purpose of steganography is to conceal and deceive. It is a form of covert communication and can involve the use of any medium to hide messages. Contrary to cryptography, it does not involve scrambling of data or using a key. Instead, it enables secret communication by hiding the message within an object, which, for the purpose of this blog, we’ll call the carrier.
One of the advantages of steganography over cryptography is that the object carrying the secret message does not attract any attention to itself — whereas plainly visible encrypted messages will undoubtedly arouse interest and may in themselves be incriminating in countries where encryption is illegal.
So, with that out of the way, let’s get on with the investigating.
I have uploaded the files examined in the blog post to a Google Drive, so you can examine them yourself with the techniques we’re going to use.
🛠 A bit of reverse engineering
The first file we’ll look at, is kfJBFkeiIAeEL.wav, (link) a seemingly normal Waveform Audio File, developed by IBM and Microsoft.
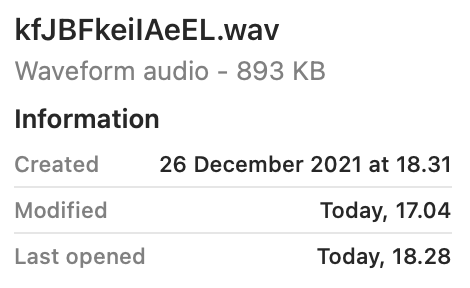
However if we click on the preview button or attempt to open the file in iTunes, nothing happens.
Although Phil Harvey’s legendary ExifTool is often only considered when analysing image files, its capabilities reach far beyond that. If we import the .wav file into the command line tool, we are faced with a ‘File format error’, indicating that the file has been tampered with or otherwise corrupted.
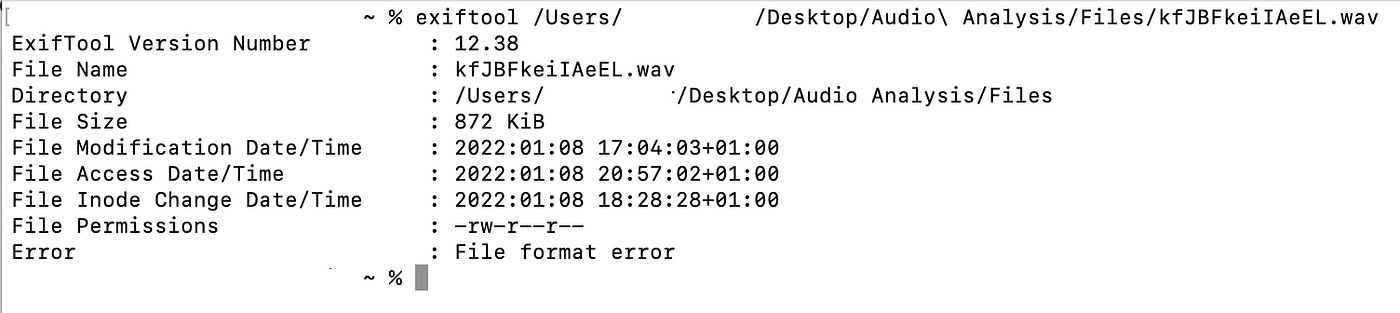
At this point, we know that the operating system correctly reads the .wav file extension, but that ExifTool is unable to output its contents. Let’s therefore take a step back and get familiar with the specifics of the file we’re dealing with.
As previously mentioned, the Waveform Audio File Format (WAV) is an audio file format standard, developed by IBM and Microsoft which uses the Resource Interchange File Format (RIFF) bitstream format method for storing data in chunks.
Like every other file type out there, audio files, too, have their own digital signature, which enables the operating system to know what program to use to run the file. These signatures start with a hexadecimal file signature that tells the operating system what kind of a file it is. A Matroska stream file for example starts with the signature 1A 45 DF A3 93 42 82 88, an MP3 file starts with 49 44 33 and so on.
If we look up the specific file signature for WAV files on filesignatures.net, we get the file signature 52 49 46 46.
Now knowing what to look for, let’s open the file in a hex editor. I use Hex Fiend, developed by Github-user ridiculousfish, but any editor should work.
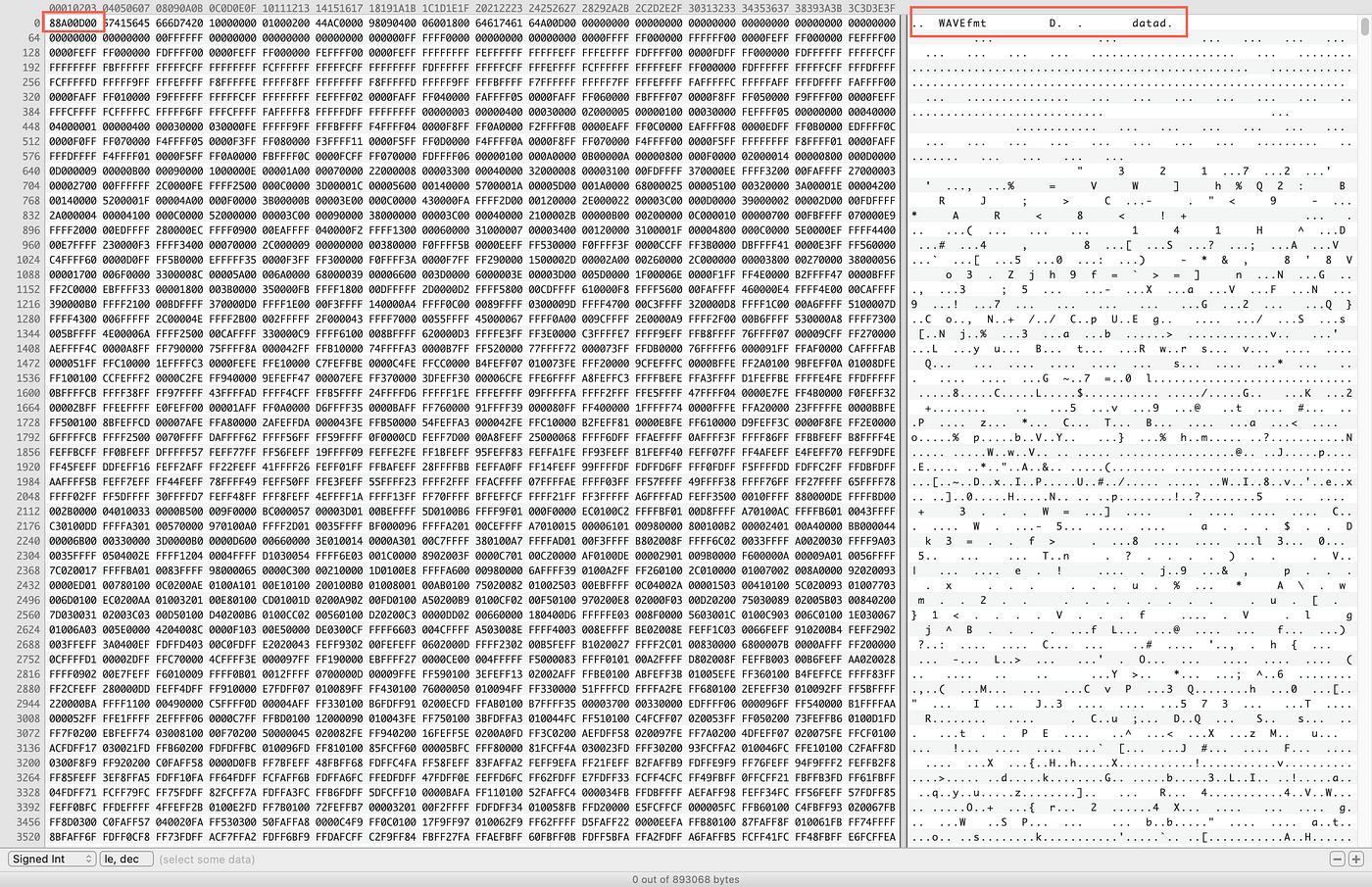
As soon as we open the file, we see that the file has indeed been corrupted. Knowing the signature for WAV files, we can easily see that the first eight letters and numbers, 88 A0 0D 00, are wrong.
A less obvious sign are the two dots in the right hand corner of the editor, indicating that there are missing ASCII characters.
By adding the correct file signature to the file, we immediately see that the file has been restored to a readable format.

By saving the file with the correction we have just made, we are now able to open the WAV file and listen to its content.
🔐 Things aren’t always what they appear to be
An even simpler, and perhaps more devious way of disguising the content of a file, is simply to change its appearance–a technique I have encountered in investigations into both criminal networks and conspiracy movements.
The file we’re going to examine, is UQSCVbeKtO.jpeg
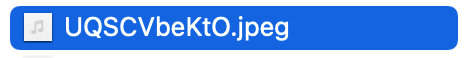
Again, the operating system recognises the file extension and displays the corresponding icon. If we attempt to open the file, much like the last carrier we examined, we get the following error:
“The file “UQSCVbeKtO.jpeg” could not be opened. It may be damaged or use a file format that Preview doesn’t recognise.”
Contrary to the previous carrier file, this time we are able to gather a lot more information about the file by running it through ExifTool, which is able to determine the File Type as MP3 and the MIME Type as audio/mpeg.
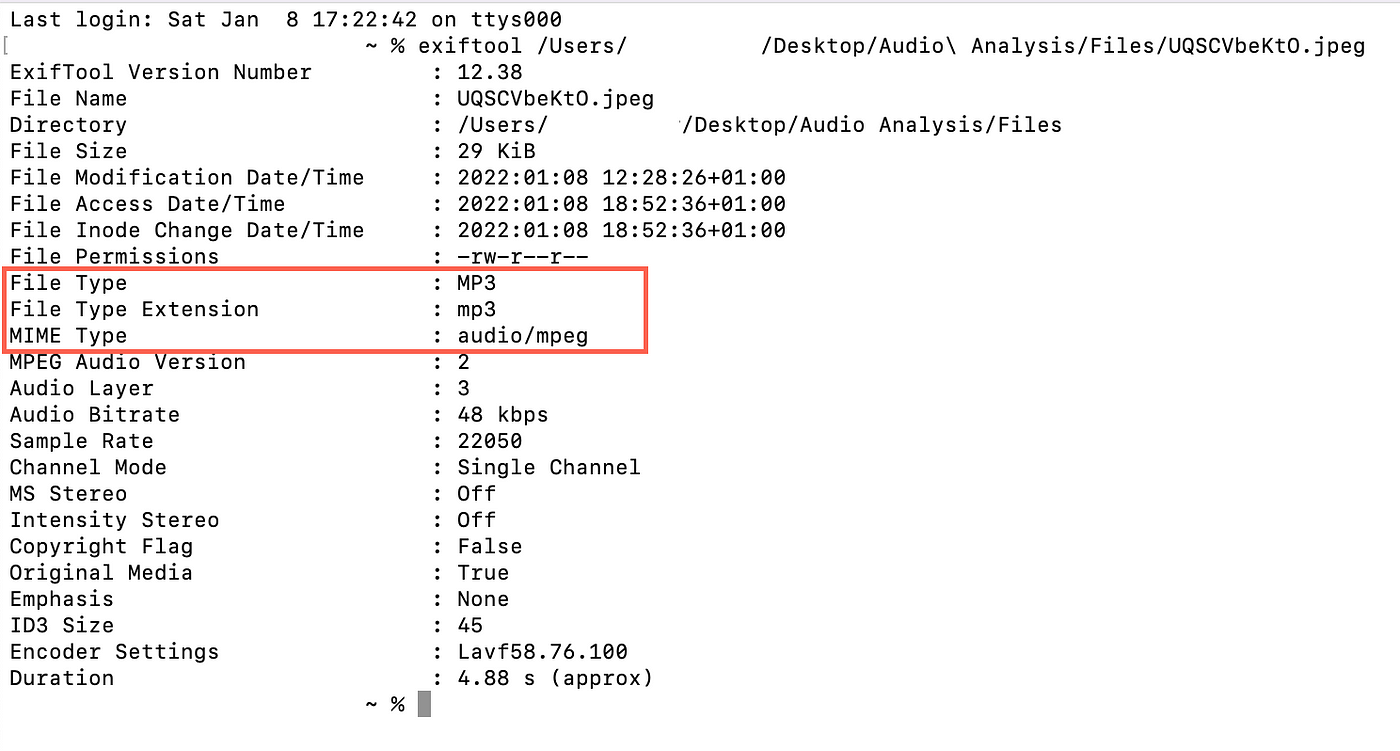
This indicates that the file hasn’t been corrupted, but that the extension is wrong, rendering the operating system unable to know which software to run in order to open the file.
Let’s help it by changing the .jpeg extension to .mp3
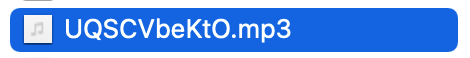
And just like that, we are now able to listen to the voice in the recording.
🔎 You see, but do you observe?
The last scenario we are going to look at, is one which, at least in my experience, is more often encountered in the context of cyber security Capture The Flag events, than in real world engagements — text hidden within the audio file itself.
In this case, the file is WNDxOKnikQ.wav.
Keeping in mind that file naming conventions can be deceiving, let’s inspect the output after running the file through ExifTool.
File Type : WAV
File Type Extension : wav
MIME Type : audio/x-wav
As we can see, the tool correctly identifies the File and MIME types and we are equally able to open the file in iTunes, although we can’t immediately understand what it is.
To examine the contents of the audio file, we are going to turn to Sonic Visualizer, a free, open-source application for Windows, Linux, and Mac developed at the Queen Mary University of London’s Centre for Digital Music.
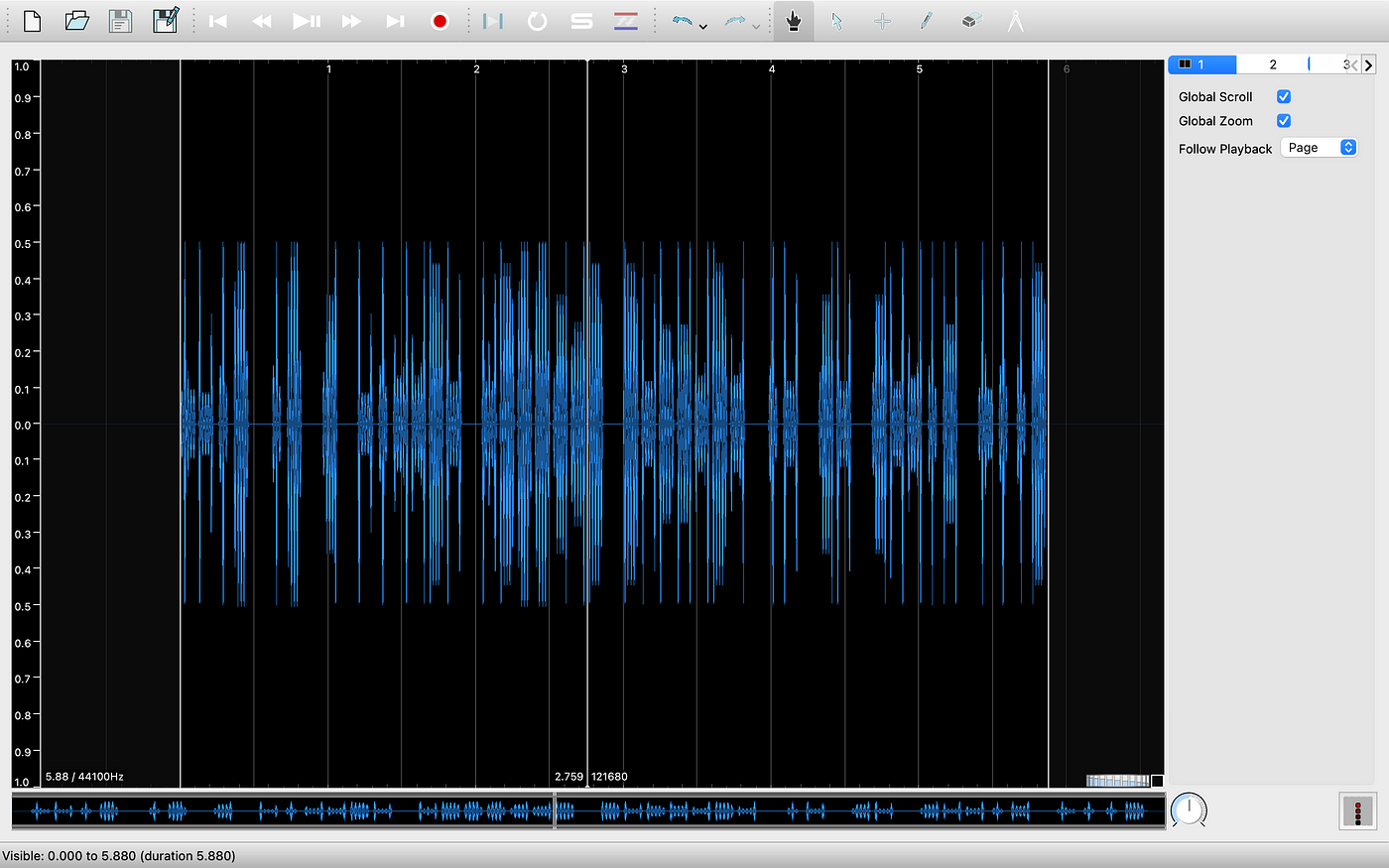
At first, all we see is a waveform rendering of the audio file. However, we can use Sonic Visualizer’s in-built Spectrogram feature to retrieve additional data from the audio file. Simply put, a spectrogram is a visual representation of the spectrum of frequencies a signal as it varies with time.
We bring up the spectrogram by hitting Shift + G.
Doing so reveals a message hidden within the audio file.

Conclusion
The three cases we have looked at here, are just a few examples of ways in which communication can be concealed within audio files, and before we wrap up, lets summarise what we now know:
The authenticity of an audio file can be verified by its unique signature on filesignatures.net
ExifTool can be used to gather additional information on a wide variety of file types, including audio files
We can use reverse engineering tools like Hex Fiend to analyse and restore damaged or corrupted audio files
Spectrographic analysis can be leveraged to reveal plaintext messages hidden in audio files
Although an operating system might recognise a file by its extension, looks can be deceiving and often require additional analysis
It is important to note though, that this list is in no way exhaustive, and that there are many examples of far more devious and damaging cases of threat actors leveraging steganography in audio files to deliver their malicious payloads.
That said, I hope this blog post has been informative and will encourage you to dive deeper into the world of Open-source Intelligence and Digital Forensics analysis.
That is is all for now, thanks for following along!
Tools and further reading
🧰 Tools
📰 Articles
WAV audio files are now being used to hide malicious code (ZDNet)
Malicious WAV files can be used to deliver malware and cryptominers (Techradar)
Rovnix bootkit returns during pandemic with new features
Waveform Audio Signature Format: Specification & WAV Recovery Example
Postagens mais visitadas
Ferramentas de pesquisa
- Gerar link
- X
- Outros aplicativos
🇧🇷 Ferramentas OSINT mais usadas por policiais no Brasil
- Gerar link
- X
- Outros aplicativos







Comentários
Postar um comentário