Welcome back, my aspiring cyber warriors!
Nearly all of us have used a search engine such as Google or Bing to find material on the web. These search engines crawl the entire web and index nearly every word contained on those pages and rank them. This enables us find the information we are looking for by simply typing in a few keywords (Google also has a special set of keywords to enable us to do Google hacking).
Now, imagine a search engine that instead of indexing the content of websites, indexed the banners pulled from each IP address (you can pull the banner on nearly every device by using Telnet or netcat). In other words, when we connect to an IP address, the device provides a banner identifying itself and some of its parameters.
Note the banner grab from a system running an Apache 2.2.22 web server on a Debian Linux operating system. This is the information that such a search engine could grab, parse and index for our search.
This information can be VERY useful for searching for vulnerable or unprotected devices. As nearly every device is connected to the Internet, such a search engine would enable us to find all the devices of a particular type (i.e. Cisco routers) or of a particular region (stoplights in California) and even SCADA systems. With so many new Internet of Things (IoT) devices entering the market place every day without proper security, such information would be a treasure trove for hackers.
Such a search engine does exist. It was developed by John Matherly in 2009 and it is named Shodan. You can find it at www.shodan.io as seen below.
Matherly's crawler scans each IP address (there are 4.3B IPv4 IP addresses) and attempts to pull and collect the banner information from each device. This information in the banner usually includes the manufacturer of the device and some key parameters. It's important to note here that Shodan indexes the data that is presented in the banner. It has no way of knowing whether the banner is accurate. Some firms that are vigilant about security actually replace these banners with fake or bogus banners to throw off Shodan or attackers. Although this is a good practice, when you start using Shodan, you will find that few actually do this.
Using Shodan
The first step in using Shodan is to register an account. You can use Shodan without registering, but the capabilities are rather limited. A basic account is free, so let's register and try some searches
Before we get started creating our own searches, let's try some that others have created and stored on the site. Among the most popular of these are web cams. Click on "Explore" in the top menu bar and it will open a page as seen in the screenshot below.
Now, let's try some of the web cam searches. At the top and center of this screen you can see "Top Voted" searches. The very first is "Web Cams". It's important to note here that each type of web cam, generally, will have unique search parameters. Remember, we are searching by the banner information and what identifies it as a web cam is usually its unique name given by the manufacturer. The point I'm trying to make is that web cam or other searches on Shodan will likely require multiple searches to capture all of the devices, unless--in the unlikely case-- that they are manufactured by one company and only have one product name.
Now with that caveat out of the way, let's get back to searching for web cams. Click on the "Web Cam" tile.
When you click on it, you will see that Shodan generates a search phrase. This phrase is comprised of the key terms that will appear in the device's banner that uniquely identify it. In this case that phrase is "Server SQ-WEBCAM". This search in Shodan delivers over 7000 IP's that meet that criteria and their corresponding devices are seen below.
We can click on any of these entries and it will take us to the Internet facing device. If we scroll down a bit to the lower part of the first page, we come to a a device in Lithuania (Lithuania is the most common residence of this particular device) as you can see below.
When we click on it, it takes us to the login screen of the web cam server. Since we know the default username and password for this particular device is "admin" and "admin" (default usernames and passwords are available all over the Internet. Just try Googling the device name and "default password" and you will find numerous entries), if the administrator left these in place without changing them, we may be able to login to their web video server.
When we try those credentials, they work! We are in!
As you can see above, we were able to access the administration panel of the web cam server with all of its controls! This system admin was definitely TOO busy to change the default credentials and now their web cam server can easily be compromised.
Webcamxp
Another interesting search within the realm of web cams is "webcamxp". These particular web cams are almost always unprotected, so that when you find one, you can simply click on the IP and begin viewing the images captured by these cams. When we put "webcamxp" into the search bar, Shodan finds over 1000 of these web cams.
Below, I have found a live image from a web cam inside a small office in Latvia. Notice the PTZ controls to the right of the camera image enabling us to zoom in or out and pan the area.
Obviously, there are hundreds of different manufacturers of web cams and you will need to know something about their banners to search for them. Usually, their banners will include the product name or the manufacturer. Try out a few.
Beyond Web Cams
The search for Internet enabled devices is almost unlimited using Shodan. As you can see below, I was able to find the login to the administration panel of a hydroelectric facility in Genoa, Italy using Shodan. Imagine what a malicious hacker could to the good people of Genoa if they could access that panel!
Shodan Search Syntax
Beside keyword search, Shodan allows us to be fairly specific in our search. We can, for instance, find devices by city, country or IP address or address range using CIDR notation. We can be so specific as to provide it with GPS coordinates, hostname, operating system and port.
Below, you can see the key terms that Shodan will accept and filter by. The syntax is simple in the format;
<keyword>:<value>
city: find devices in a particular city
country: find devices in a particular country
geo: you can pass it coordinates
hostname: find values that match the hostname
net: search based on an IP or /x CIDR
os: search based on operating system
port: find particular ports that are open
before/after: find results within a timeframe
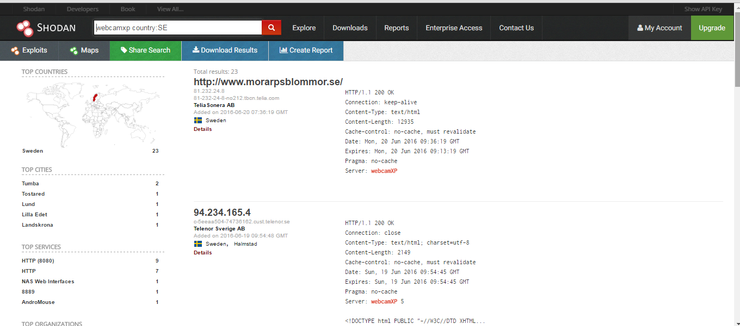
So for instance, if I wanted to find webcamxp in Sweden, I could type in the search window;
webcamxp country:SE
Or, if I want to find webcamxp in Sweden and only using port 8080, I can construct a query like;
webcamxp country:SE port:8080
Or, we could look for webcamxp in Sweden on the telia.com host by entering;
webcamxp country:SE hostname:telia
Or, we could look for those webcamxp's in Sweden on the subnet 81.229.0.0./16 by entering;
webcamxp country:SE net:81.229.0.0/16
As you can see, the Shodan search filters enable us to be VERY specific in finding Internet connected devices.
More Shodan
In addition, Shodan has an API that enables us to connect other applications-- such as recon-ng-- to Shodan to use its resources and capability. This API requires that you open a premium account to access and these go from $19/month to $99/year. In future tutorials here on www.hackers-arise.com, I 'll show you how to find traffic signals, routers, home security systems, refrigerators (?) and just about any kind of device connected to the Internet, so keep coming back to Hackers Arise to learn the most valuable skillset of the 21st century--Hacking!
For more Shodan, check on my tutorial on using Shodan to find SCADA/ICS systems or using Shodan in conjunction with Metasploit by using AutoSploit.
To learn more about using Shodan to find vulnerable systems, check out Shodan, Part 2.



























Comentários
Postar um comentário