Compartilhe
- Gerar link
- X
- Outros aplicativos
Using OSINT for Maritime Intelligence

@lumena-mukherjeeLumena Mukherjee
I'm a cybersecurity consultant, tech writer, and a regular columnist for InfoSec Insights.
According to Naval Dome, the maritime industry has seen a 900% increase in cyber-attacks since 2017
Better late than never seems to be the motto being followed by the International Maritime Organization (IMO), which issued a deadline of January 2021 to shipowners and operators to address cyber risks in existing safety management systems (SMS). In 2013, Trend Micro, a cybersecurity firm in Japan, demonstrated how the automatic identification system (AIS) used by ships to broadcast their identity and position, could be manipulated and compromised. Besides AIS, which continues to be unencrypted and loaded with security flaws, even the rest of the OT infrastructure used in the maritime industry hasn’t kept up with evolving cyber risks. Let’s take a closer look at some of the systems that can potentially come under attack.
Cyber Risks in the Maritime Industry
The shipping giant, Maersk, fell victim to the NotPetya malware in June 2017, which resulted in financial losses of up to USD300m. It brought 76 port terminals across the world, and its container ships at sea to a halt. COSCO shipping lines, and Austal (an Australia-based ferry and defense shipbuilder), were also hit by a cyber-attack in 2018.
When we’re talking about cyber risks in the maritime industry, we need to consider not only information security risks that compromise the confidentiality of data, its integrity, and availability but also risks to operation technology (ICS/SCADA) systems. Some of the systems that might get impacted are as follows:
- Navigation systems (ECDIS, Radar, GPS, etc.) can be manipulated using jamming and spoofing techniques.
- Communication systems (sat link, AIS, GSM, etc.) can be targeted by attacking the wireless link.
- Loading and stability of the ship can be modified by manipulating the EDIFACT messages to destabilize ships, cause delays at ports, change price details, etc.
- Global Maritime Distress and Safety System (GMDSS) sends or receives distress alerts from ship-to-shore, shore-to-ship, and ship-to-ship. According to IOActive, terminals running on the insecure ThraneLink protocol are prone to attacks.
- Ship and crew networks are often not properly segregated and can be compromised via email, social engineering attacks, malware downloads, etc.
- Sensors (temperature, pressure, level, current, anemometer, etc.) connected to the shipboard LAN, if compromised, can lead to misrepresented data on the ship’s Electronic Chart Display and Information Systems (ECDIS).
- Third-party updates and remote access to service providers on the shoreside can also be one of the attack vectors.
AIS, used for collision avoidance and traffic monitoring, receives the location data from GPS (or any location-sensing technology) and then broadcasts this information to nearby ships and onshore receivers. GPS manipulation and spoofed AIS data can make ships appear or disappear and create ‘ghost’ ships that could ultimately lead to collisions or unplanned changes to a ship’s route to avoid one. They can also cause a distorted view of commodity flows, supply and demand at ports, impact trading models due to false data, etc.
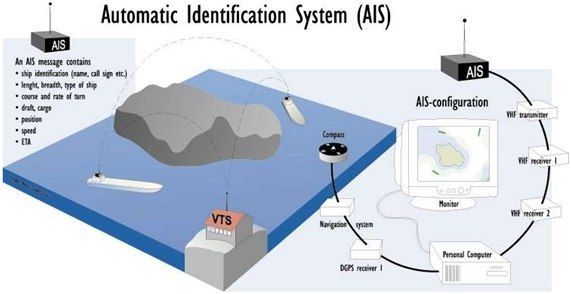
Figure 1: Working principle of AIS; Image Source: https://aulanautica.org/wp-content/uploads/2015/03/TEMARIO-PY-140.jpg
The shipping industry has been known to be vulnerable to GPS jamming and spoofing attacks. South Korea reported the return of 280 vessels to port due to problems in their navigation system in 2016, while, more recently, in 2019, spoofing attacks on hundreds of vessels were carried out in China.
Even without manipulating signals, sending phishing emails, or hacking into these systems using various channels, an attacker can collect a lot of information about their target merely by searching the internet. This information can be put to good use in the later stages of an attack.
Leveraging OSINT to Gather Ship Data
OSINT refers to Open Source Intelligence that relies on publicly disclosed resources to gather information about an entity of interest. The information collection process is carried out passively without any direct contact with the target. Public resources such as blog posts, social media sites, discussion boards, etc. are typically used though more specialized tools such as Shodan, Maltego, etc. can also be deployed.
Shodan is a powerful search engine for IoT devices. It can not only find VSATs, comm boxes, etc. but also list open ports on these devices and
vulnerabilities based on their technology stack. The screenshots below are from a Very Small Aperture Terminal (VSAT) device that discloses information such as the exact location of the ship, the vessel’s name, etc. Entering the latitude and longitude information on Google Maps pulls up the image of the ship on sea, nearby ports, etc.
vulnerabilities based on their technology stack. The screenshots below are from a Very Small Aperture Terminal (VSAT) device that discloses information such as the exact location of the ship, the vessel’s name, etc. Entering the latitude and longitude information on Google Maps pulls up the image of the ship on sea, nearby ports, etc.
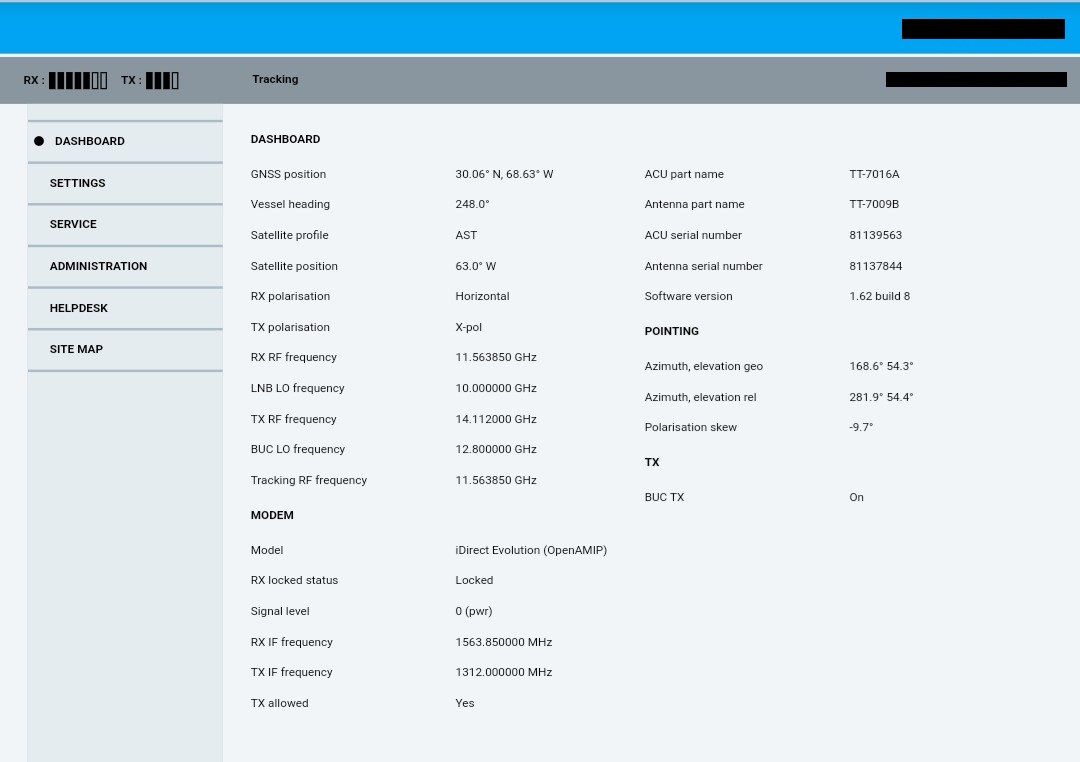
Figure 2: VSAT Dashboard of a Ship
The user login and administration screens can also be accessed. A simple google search can be used to find the default credentials (admin/1234, in this case). Considering that most of these devices do not use SSL certificates, do not update their software versions or run on outdated hardware components, there is a fair chance that many of them would not have changed the default login credentials.
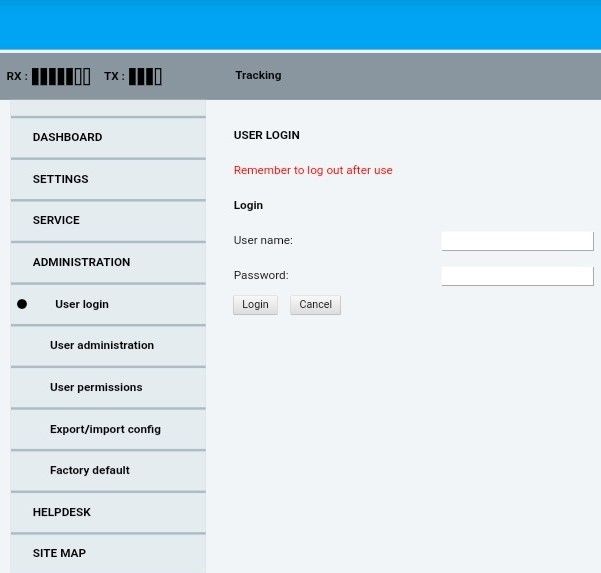
Figure 3: Login Screen
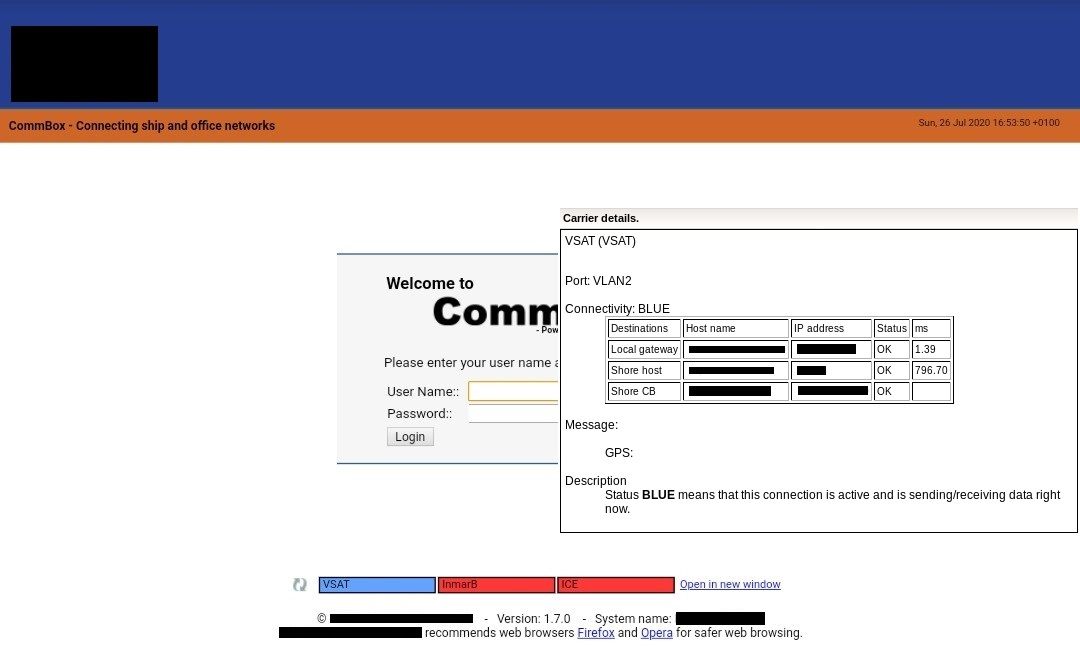
Figure 4: A CommBox with network config information revealed by hovering over the VSAT tab.
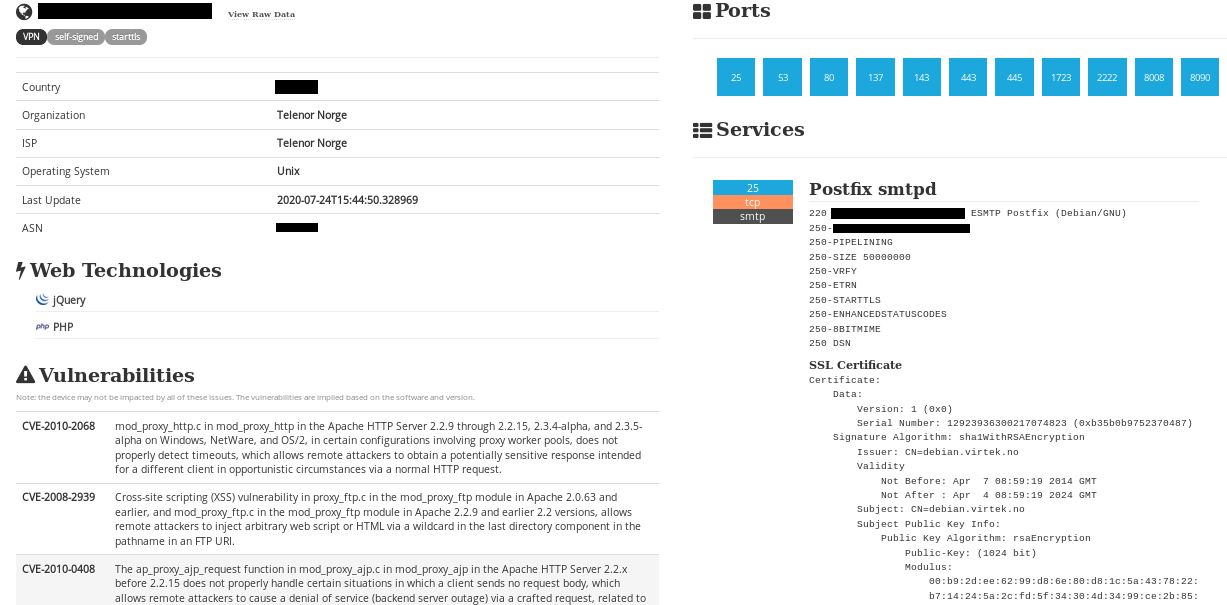
Figure 5: Vulnerability list and open ports from a VSAT on Shodan
Other details such as the flag under which the ship is sailing, call sign, IMO number, other vessels close to it, etc. can also be found using websites like MarineTraffic, VesselFinder, etc. They also feature a live tracking map that plots all the ships out on the sea and whose details can be obtained by clicking on an arrowhead.
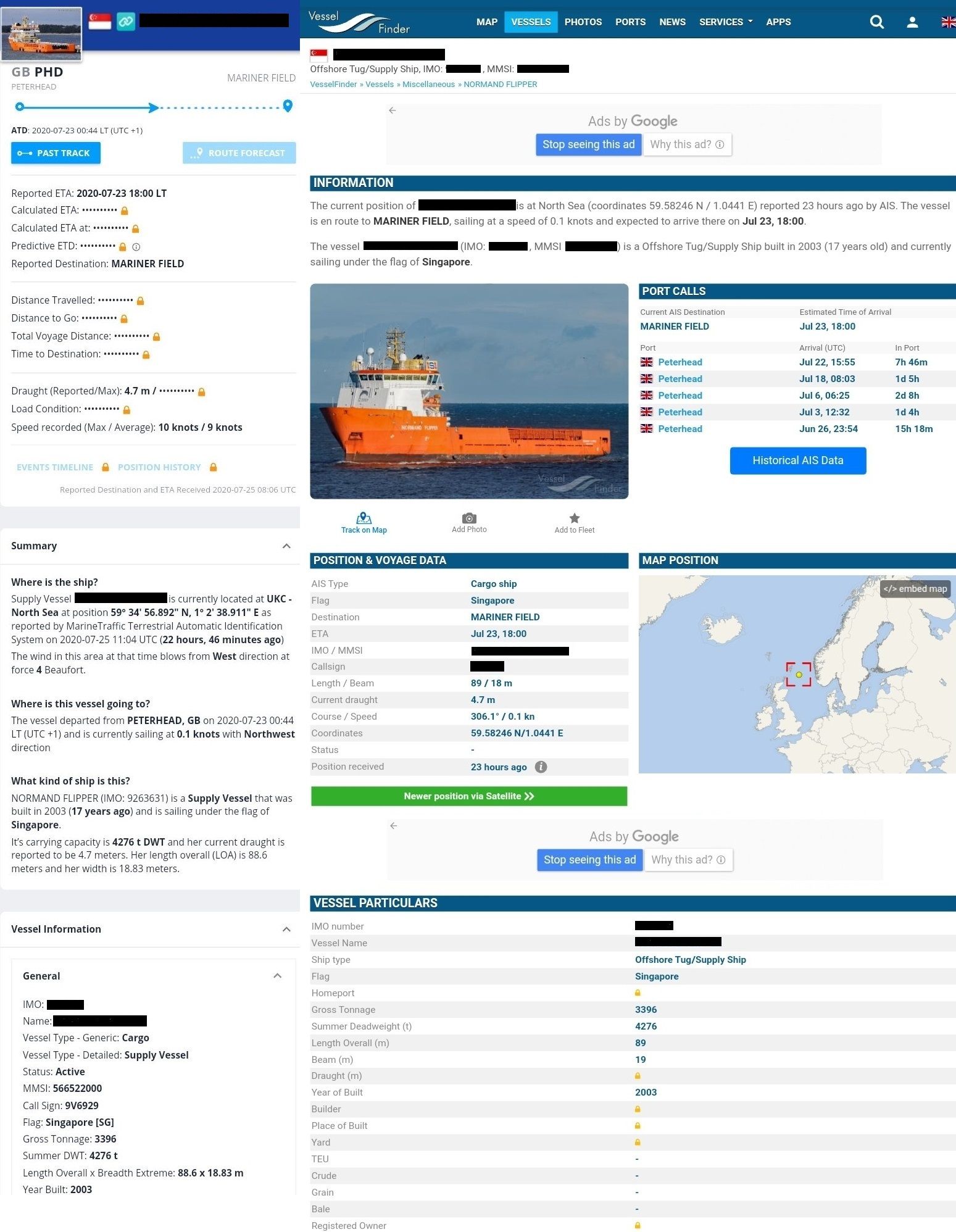
Figure 6: Ship Details
Any malicious actor can launch an attack by sending phishing messages or emails to the crew currently working on these ships. Most of them have access to emails, messaging apps, or can be found via social media. The crew network is not always properly isolated from the ship network, and a foothold can potentially be gained via this channel. At the very least, there is a decent chance to phish the credentials used by the target crew member, especially if additional OSINT is done. MyShip is one such networking platform for seafarers running over an unsecured HTTP connection.
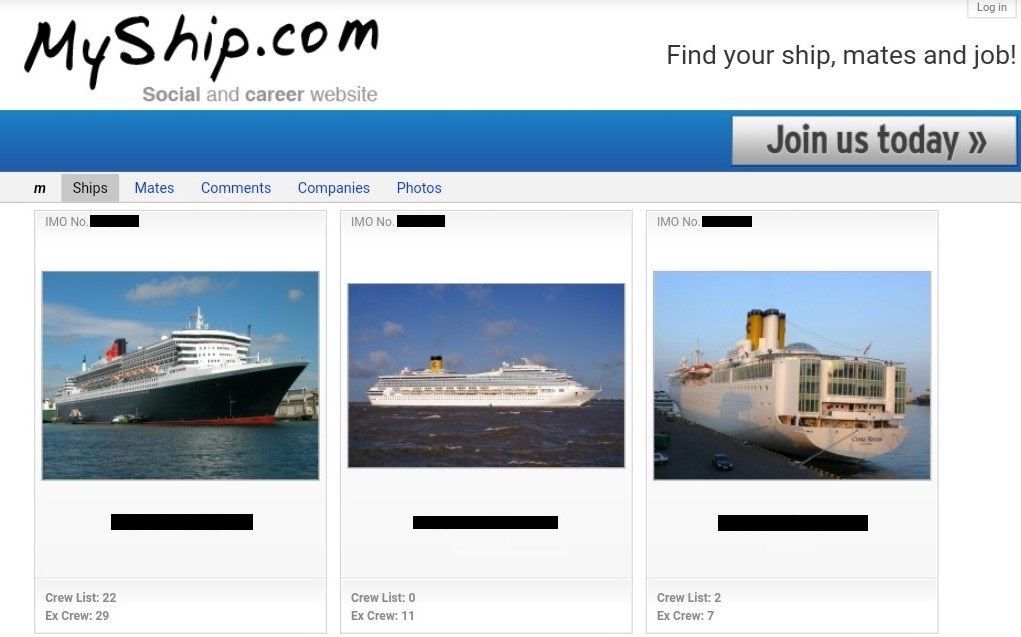
Figure 8: MyShip Portal
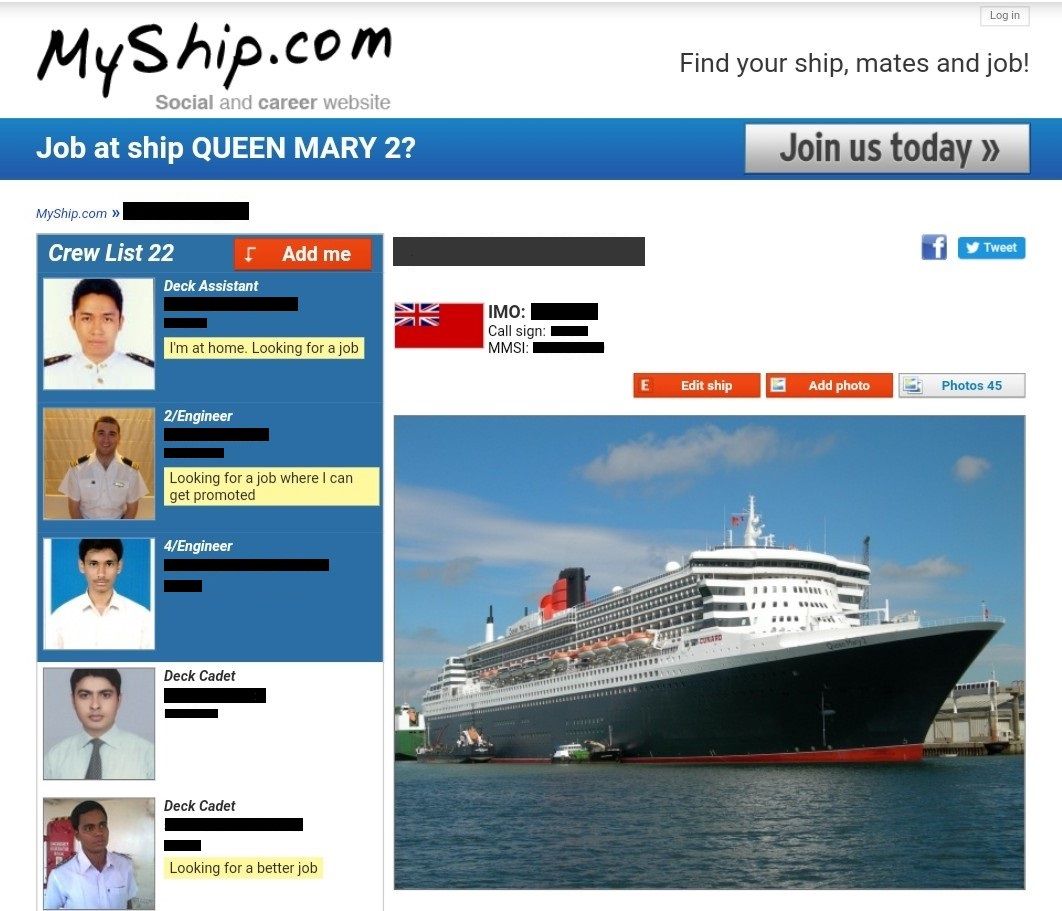
Figure 7: Crew member listing
Wrapping Up
According to a study done by Futurenautics in 2018, just under half of the active mariner respondents claimed to have sailed on a vessel compromised by a cyber-attack, and only 15% of seafarers received any form of cybersecurity training. These numbers are indicative of a general lack of awareness on safe security practices that can be improved through training and workshops. What will prove challenging is discontinuing obsolete components and upgrading systems to patch vulnerabilities, given that a ship’s operation technology can have dire physical impacts from accidental or malicious modifications.
Comments
Postagens mais visitadas
Ferramentas de pesquisa
- Gerar link
- X
- Outros aplicativos
🇧🇷 Ferramentas OSINT mais usadas por policiais no Brasil
- Gerar link
- X
- Outros aplicativos






Comentários
Postar um comentário