Compartilhe
- Gerar link
- X
- Outros aplicativos
Maltego Dorking with Search Engine Transforms Using Bing
 Andrew Fordred
Andrew FordredMost of us make use of the practice of Dorking, commonly known as Google Dorking, when applying OSINT. Some loath it but know it has to be used at some stage, and others cannot operate without it. In theory, it is not only applicable to the Google search engine, but also to Bing, Yandex and others. This brings us to Maltego.
Maltego provides a number of search engine Transforms that make use of the Bing API. These Transforms return the search results of Bing for a given input query. In this tutorial, we will be demonstrating how you can use certain search attributes to significantly increase the relevance of returned results or narrow down the search focus in Maltego.
How Does Maltego Dorking with Bing Work?
Maltego Dorking works with several Entities. In this example, we will demonstrate Dorking with the Phrase Entity.
Using the Phrase Entity, we search for the term “cisco” using the To Website [using Search Engine]Transform. With the results setting set to maximum, we get the following:
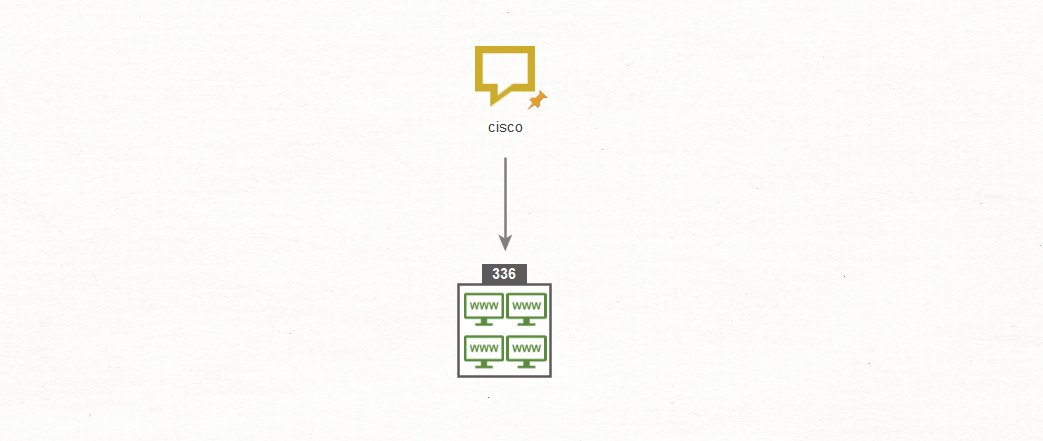
The results are a lot to deal with, even if compared to the 220 million results for the same simple search in Google or the 58 million results in Bing. If we explode the collections box in Maltego, we would have to work through the results to find relevancy to whatever research or investigation we may be doing at the time.
A nice thing the results have, is a number of associated websites/sub-domains, which is great information for blue teams or pentesters.
Increase Search Result Relevance with Quoted Search Terms
One way to increase search result relevance is to add quotation marks around the search terms. Especially useful for phrase searches, this ensures that the search engine only searches or filters for a specific word or sentence, meaning a result is only returned when the words or sentences appear as an exact match.
If we use the quoted search terms “cisco” and “Chuck Robbins” (the CEO of Cisco), Maltego returns the following results:
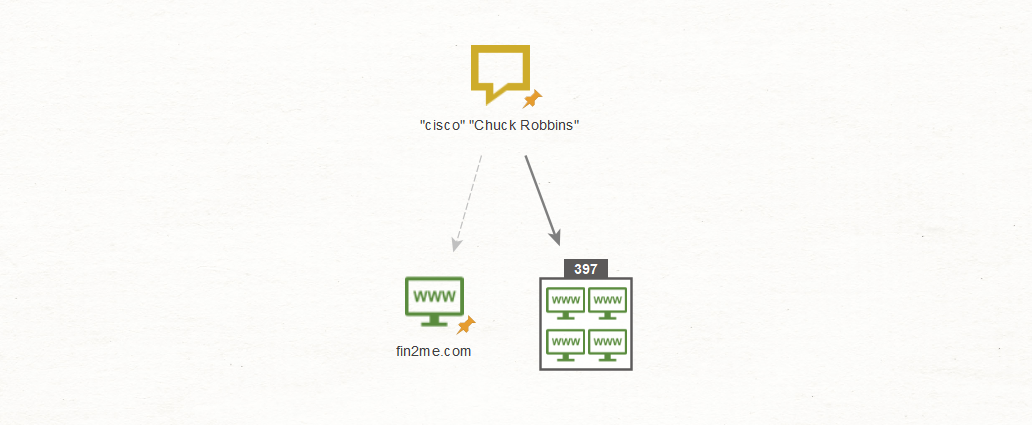
Yes, it did increase the number of results to 397, which means more individual results to comb through. However, working through the results, it is surprising how accurate they all are. The reason for this is that as Bing puts together the two terms — “cisco” and “Chuck Robbins”— it only returns content containing both terms.
To illustrate, let us conduct a search for the website www[.]fin2me[.]com and use the Transform To URLs [show Search Engine results] to extract the articles we may be looking for from said website.
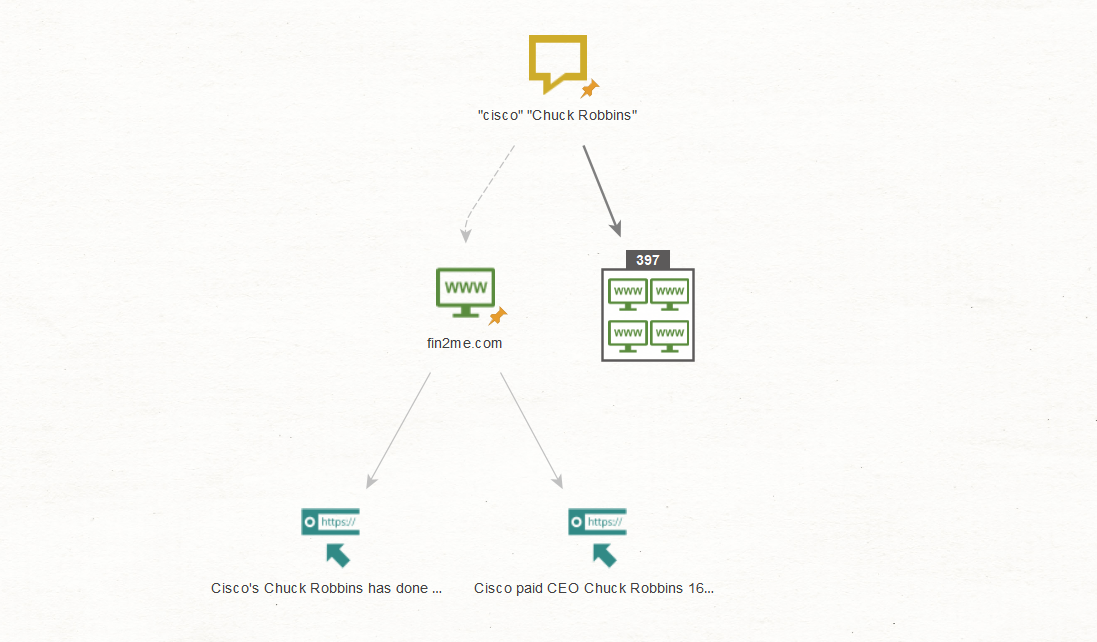
The Transform extracts the two articles from the website which match Cisco and its CEO Chuck Robbins. To confirm relevance, we can simply look at Maltego’s snippet window in the Detail View, which shows that we are on the right track.
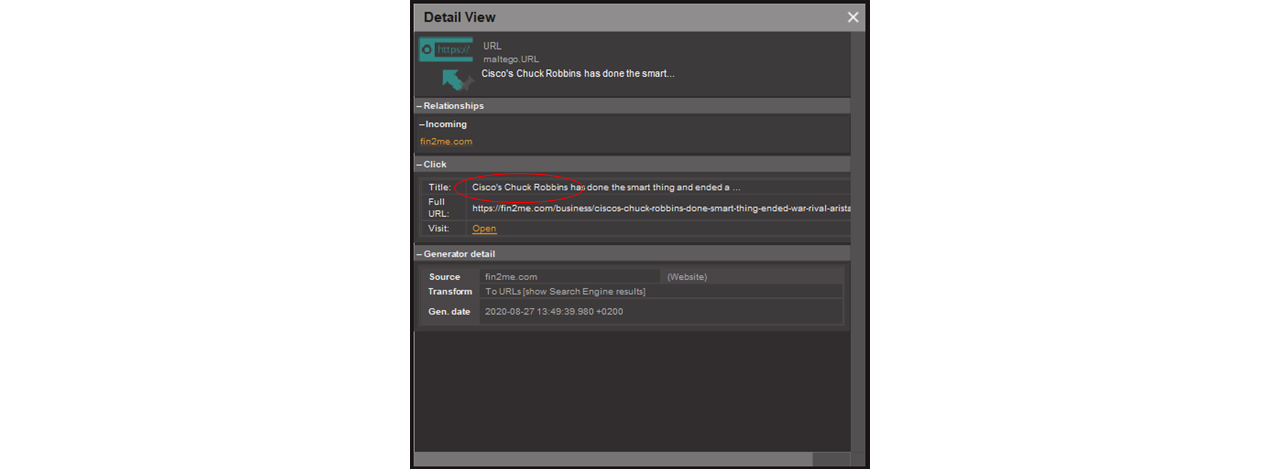
That was easy enough. While Maltego has done most of the heavy lifting already, there is a lot more analysis that Maltego can help us with.
Extract Specific Search Types using Search Operators
Next, we repeat the same process for the terms, “cisco” and “confidential”:
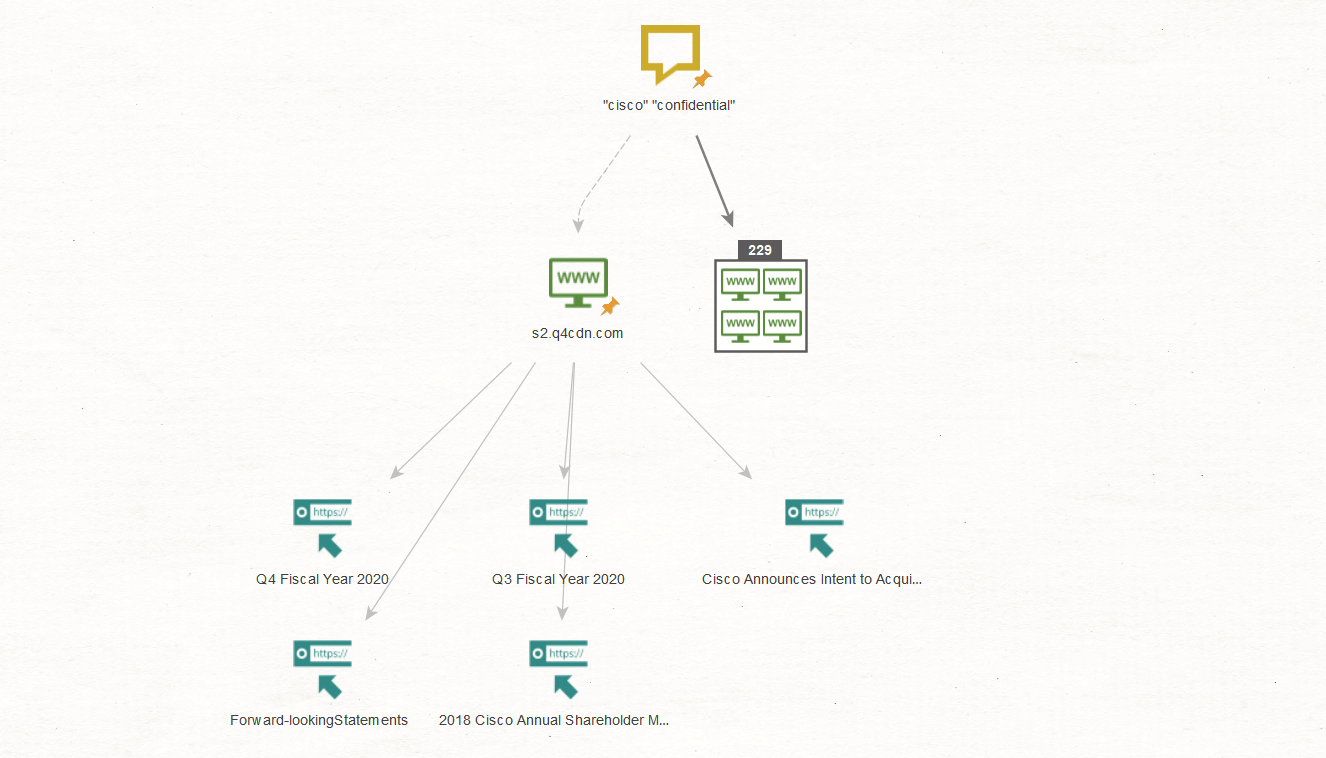
The extracted URLs contain links to documents or information that may have been classified as confidential, which is excellent data for anyone performing anything from blue to red to black teaming, not to mention the bad guys.
For Maltego to return only search results in a specific format following the previous process, we must include a search operator. Different to a search term, a search operator is a string of characters used in a search query to narrow the focus of the search.
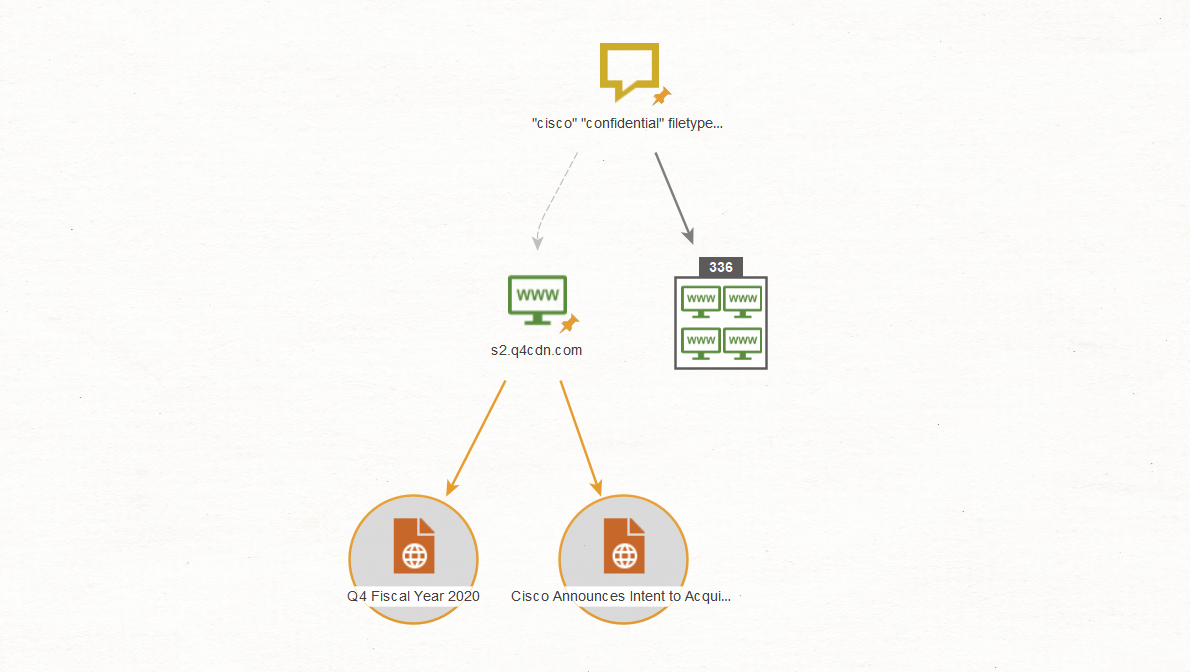
For example, looking specifically for PDF documents, we input the search operator “filetype:pdf” and run that search again using the To Website [using Search Engine] Transform:
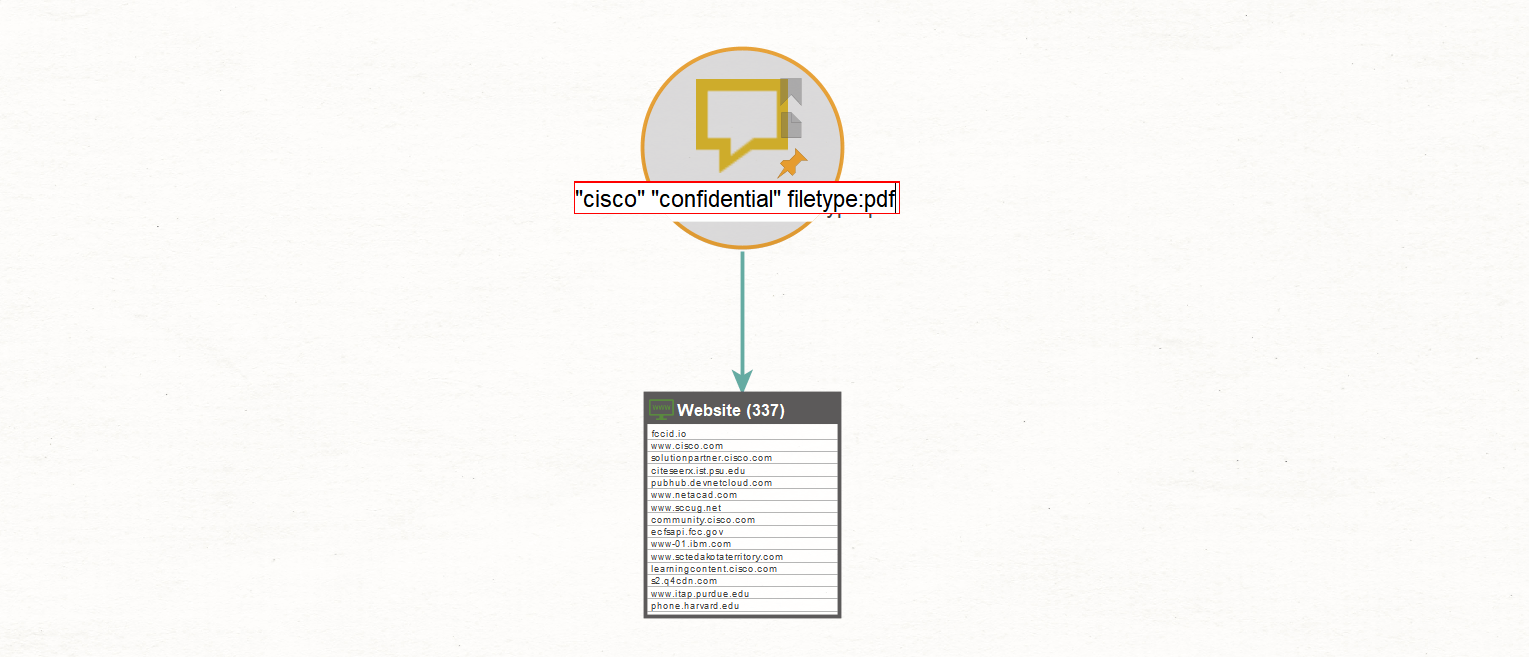
Now, using the URL extraction on the same site as above (www[.]s2[.]q4cdn[.]com) will provide those URLs containing only PDF files:
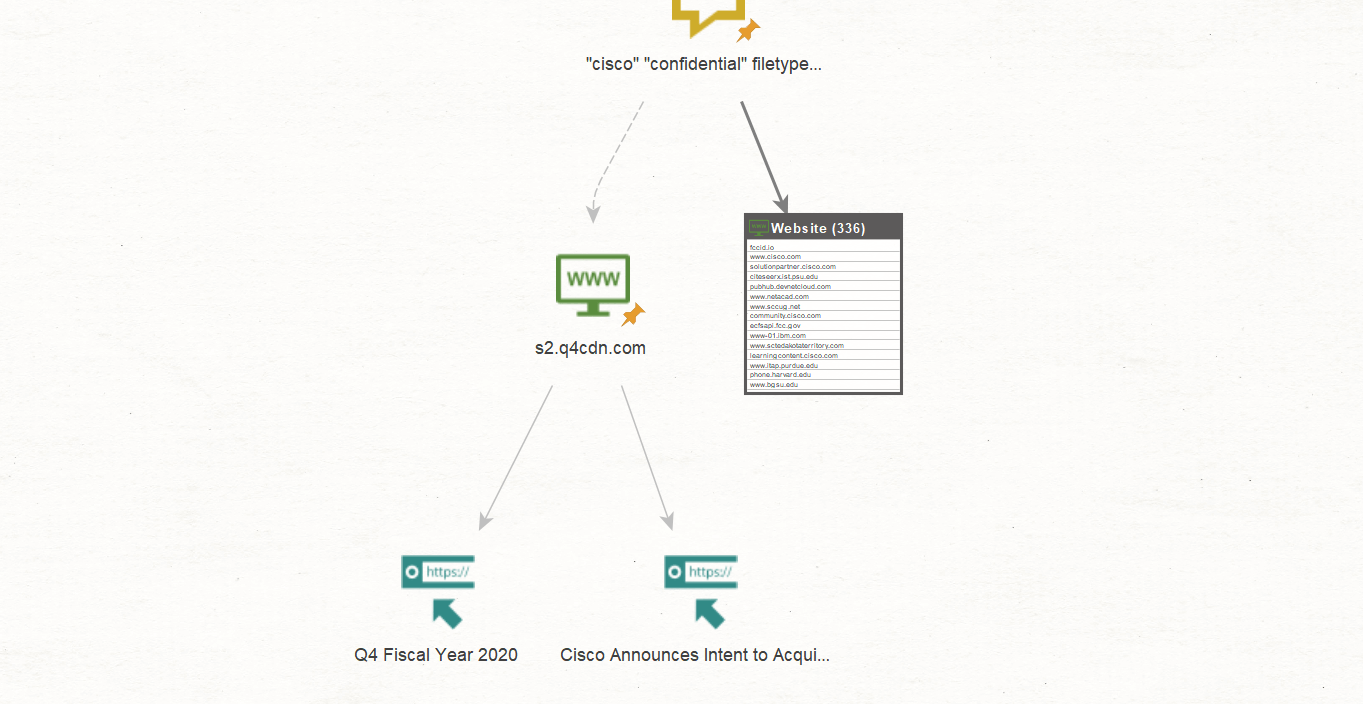
Now, we select both URL Entities, right-click to call out the Context Menu, and change them to Document Entities using the Action bar below:
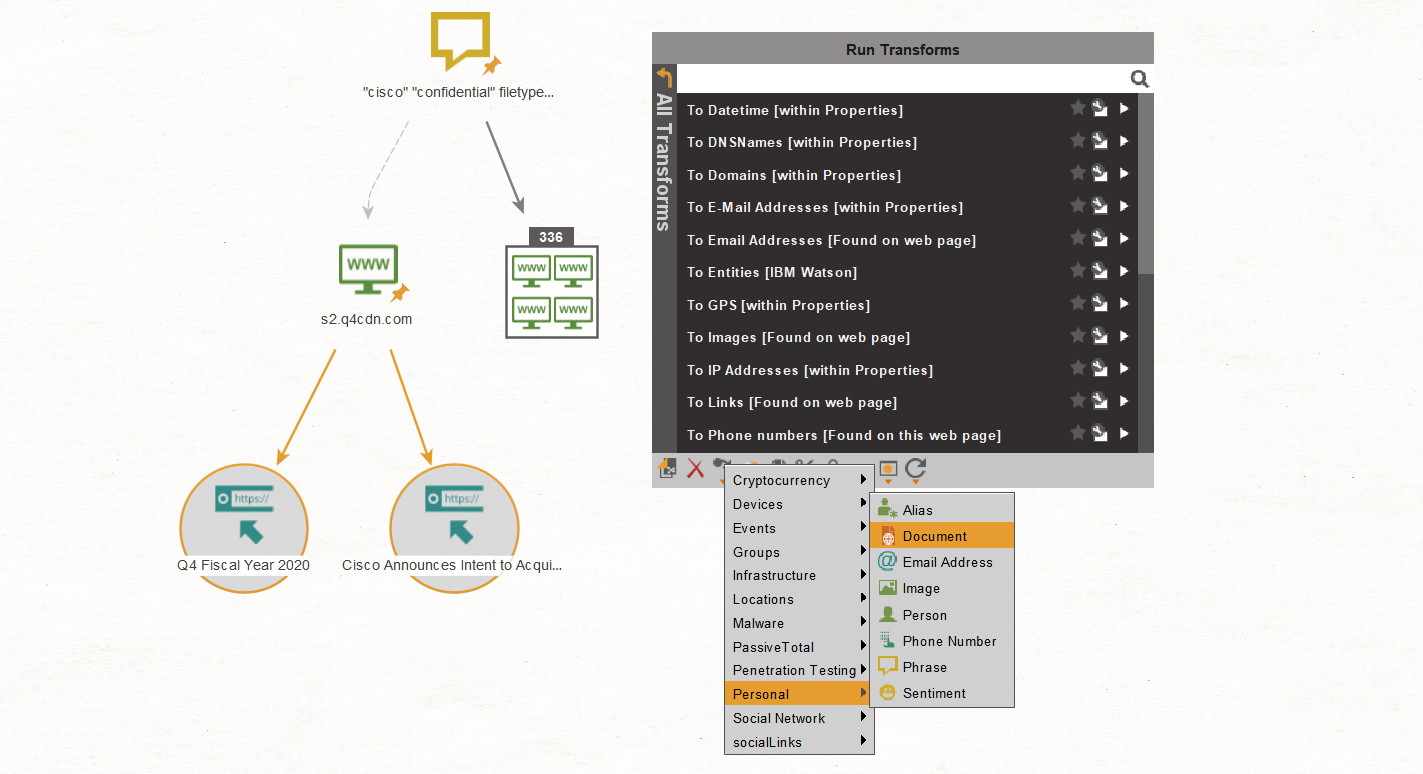
The result should look like this:
Selecting both Document Entities, we run the Parse meta information Transform, which performs similarly to FOCA or metagoofil:
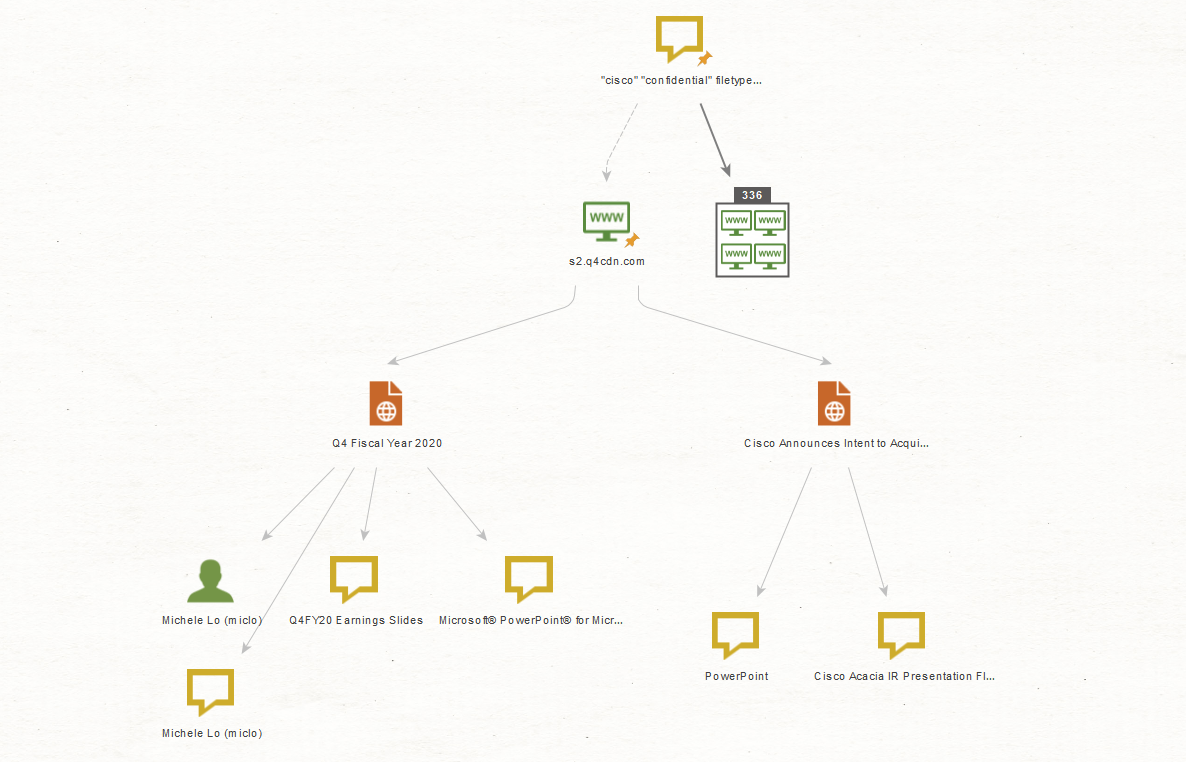
Whoa, how long would this take in real time!
In just a few minutes, the basis of an attack has been set and we have a person’s name and document titles. This could be used for social engineering, payloads and more. Although we show a small-scale example, it could be escalated into a more serious scenario with some more time invested into getting even better results, which could establish some devastating pivot points against a target.
But wait, we’re not done Dorking just yet.
Return Specific Search Results with Site Operator
Using the “site:” operator, we run the same process again. The “site:” operator allows us to see the URLs indexed for a specific website.
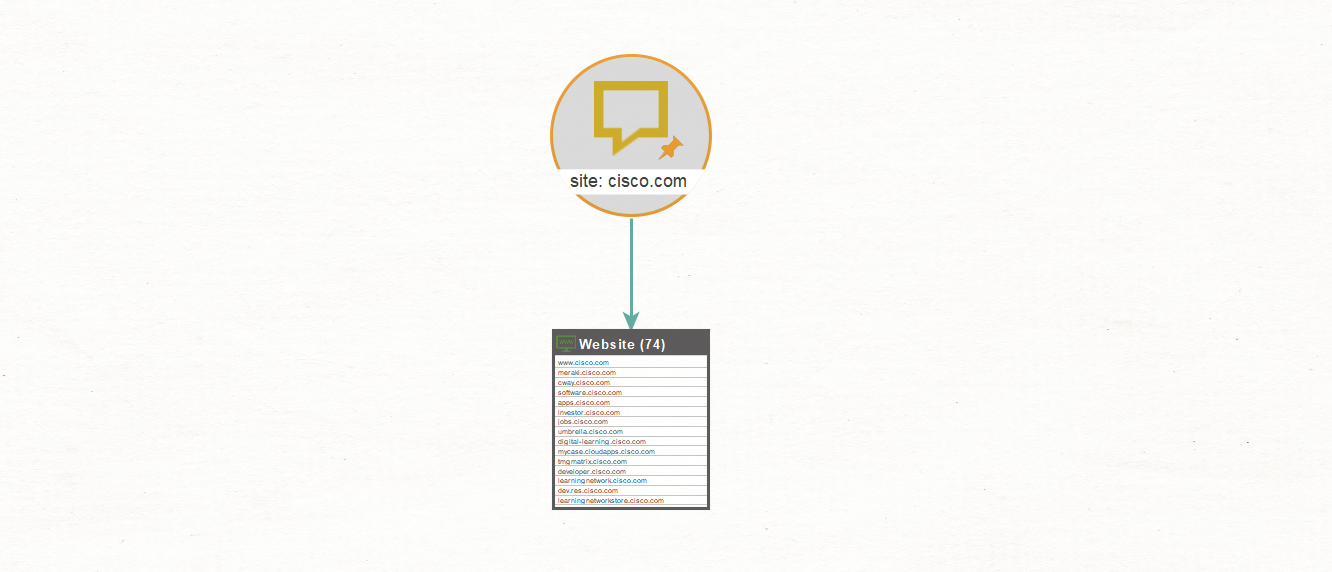
Not only did this Transform return the site www[.]cisco[.]com, it also returned any other website address containing cisco[.]com that has been indexed by Bing. You could even tackle this again by adding the filetype:pdf operator and the results will contain all the PDF files on the site www[.]cisco[.]com or a variation thereof.
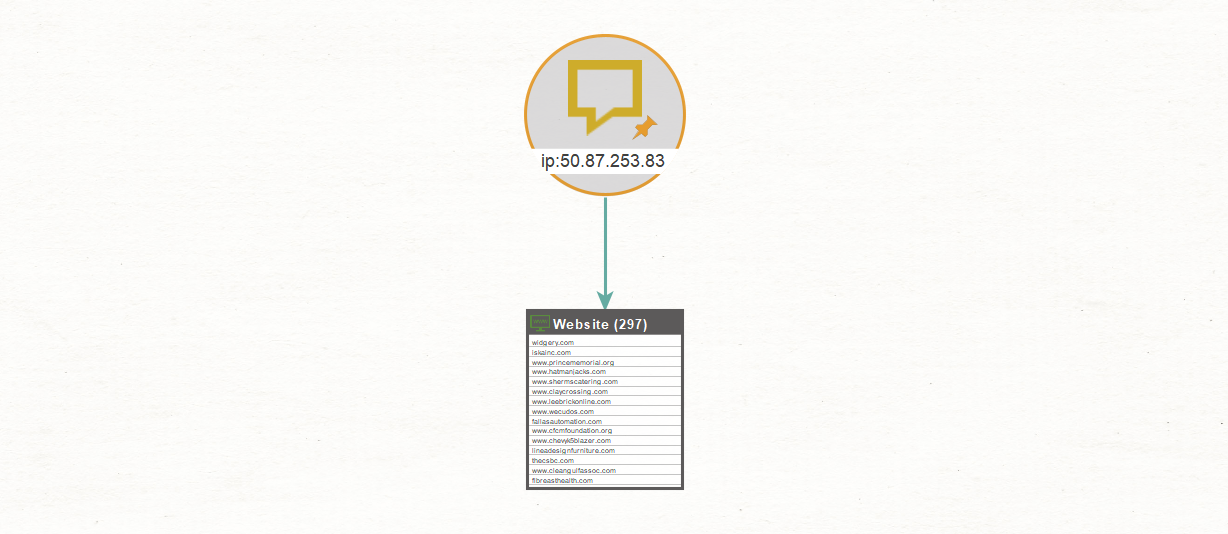
Using the IP Operator Exclusive to Bing
The one dork or operator that Bing has that is not supported by Google, is the IP operator. The search on ip:50.87.253.83, for example, would result in 297 websites linked to that IP address.
Search Social Media Sites with Site Operator
This type of Dorking can also be used for searching social media sites, for example: “cisco” site:twitter.com
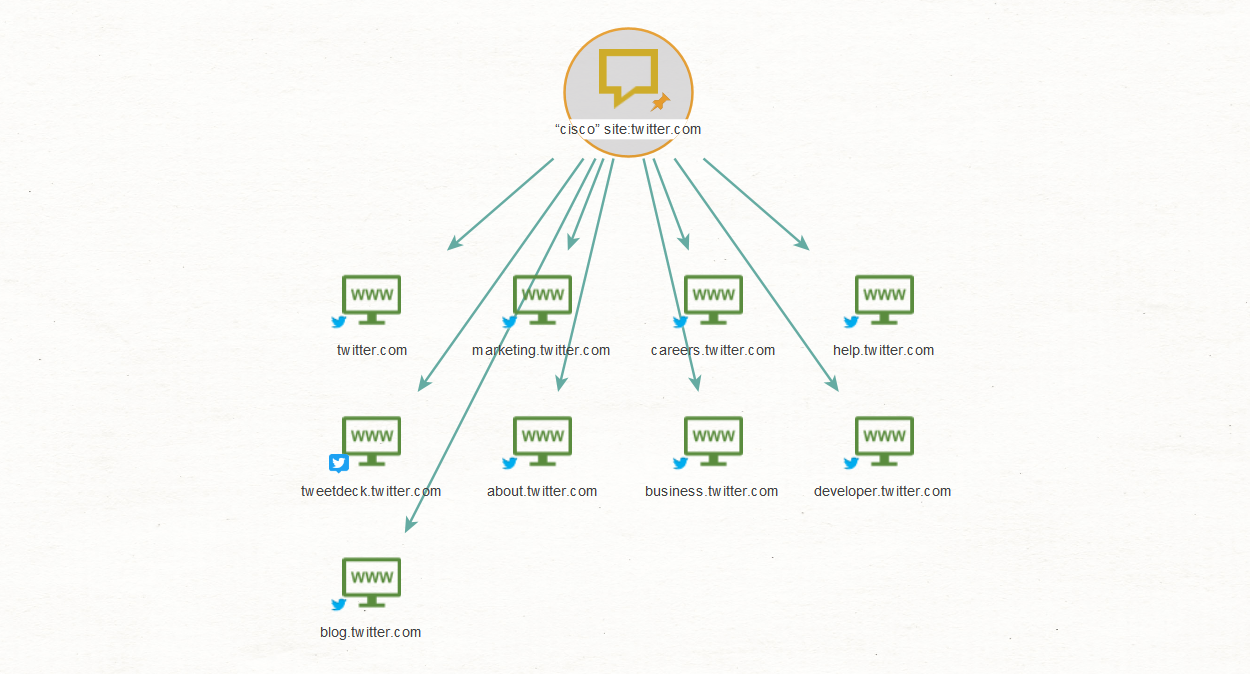
Lastly, you may want to include a variation of social media platforms in your searches, for which you can use the OR operator e.g. “cisco” site:twitter.com OR site:facebook.com OR site:linkedin.com
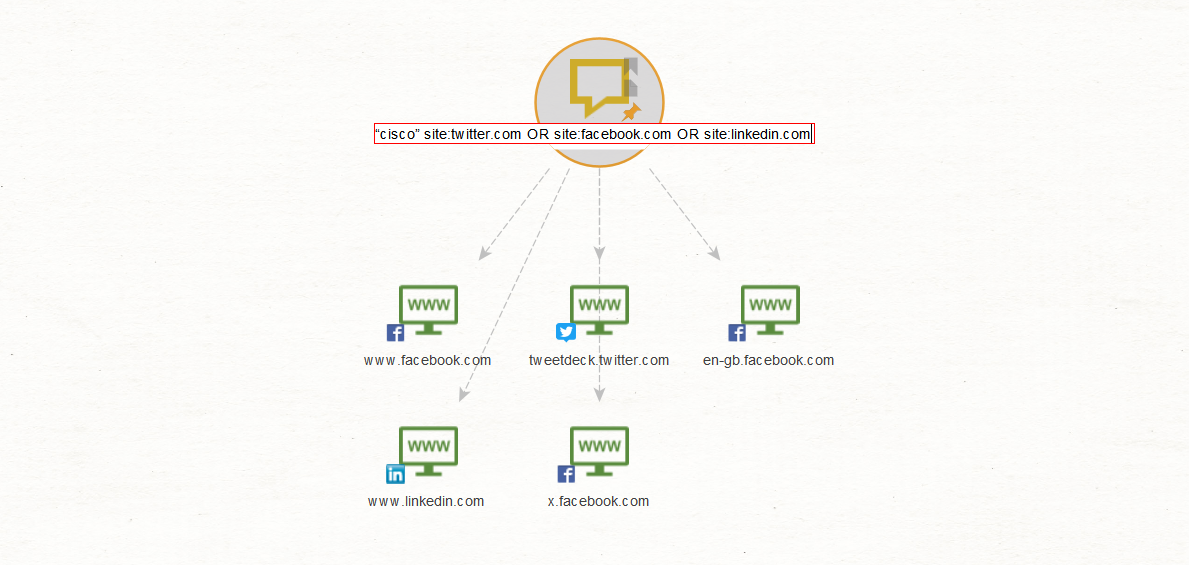
While the results may appear to be few, the accuracy of the search has been increased exponentially by using a specific search term of cisco together with the site operator. In addition, as described above, some of the website results could contain a lot of URLs linking to the exact issues we may be searching for. We only need to extract them.
This concludes our brief overview on using the humble dork in Maltego. With this method and technique in mind, the sky is the limit for the online researcher, investigator or anyone from the infosec disciplines.
About the author
Andrew Fordred
Andrew Fordred, a Namibian, previously served as an intelligence officer for the Crime Intelligence Service assigned to the Organised Crime Intelligence Unit of the South African Police. After leaving the police service, he held a number of corporate positions in capacities such as Risk Management, and later, forensic investigations. In 2007, he started his own business providing forensic investigations, intelligence, risk management consultancy, court testimony and litigation support. He completed a forensic investigation degree focusing on forensic intelligence with a qualitative case study of the illegal narcotics trade and syndicates. Currently, he is providing due diligence, cyber intelligence and investigations, cyber security and privacy, and training services to clients with emphasis on open source intelligence, social engineering and the dark web. In addition, he has been a public speaker at events such as the Journey of the Hacker Windhoek Namibia, OSMOSIS 2018 Las Vegas USA and Cyber Threats against Children UNICEF. Reach out to him on Twitter or LinkedIn.
- Gerar link
- X
- Outros aplicativos
Postagens mais visitadas
🇧🇷 Ferramentas OSINT mais usadas por policiais no Brasil
- Gerar link
- X
- Outros aplicativos
Comandos Google Dorks
- Gerar link
- X
- Outros aplicativos
Top 10 Popular Open Source Intelligence (OSINT) Tools
- Gerar link
- X
- Outros aplicativos
Gmail OSINT: Como investigar contas do Gmail com ferramentas OSINT
- Gerar link
- X
- Outros aplicativos
OSINT APLICADO À GOVERNANÇA
- Gerar link
- X
- Outros aplicativos
Operação Epic Fury , ⚠️ SITUAÇÃO CRÍTICA — CONFLITO ATIVO EM TEMPO REAL
- Gerar link
- X
- Outros aplicativos
How to Install Kali Linux NetHunter Rootless on Android (No Root Needed!)
- Gerar link
- X
- Outros aplicativos



Comentários
Postar um comentário