Sn0int is a semi-automatic open-source intelligence (osint) project. The framework collects publically available information followed by data processing and mapping. The framework has a lot of interesting osint features. Some of these features include:
- Human profiling across the internet
- Phone numbers information collection
- Image scanning
- Instagram data and images collection
- Discovering compromised logins in breaches
- Bypassing Cloudflare via shodan
- Email collection from PGP servers and WHOIS record
- Domains IP and GEOIP address collection
- Harvesting subdomains through Passive DNS and certificate transparency logs
- Local networks enumeration
Sn0int has a default set of modules to perform the aforementioned tasks. The framework gives the freedom of writing and integrating our own modules. Penetration testers can even publish their modules to make them available for other Sn0int users.
Sn0int Installation
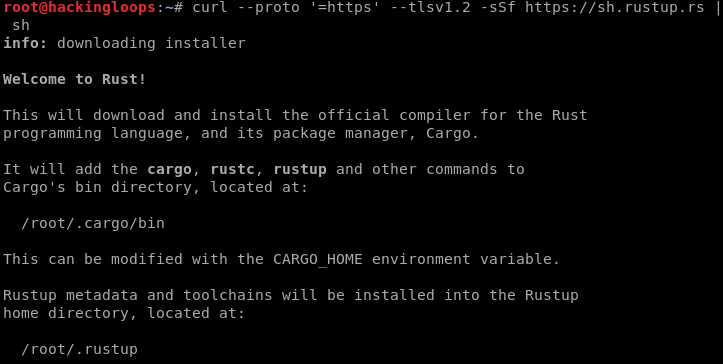
Sn0int depends on Rust (programming) and few other packages. Rust can be installed by typing the following command in the terminal.
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
The above command automatically installs cargo –the package manager for Rust. Cargo is responsible for downloading Rust package’s dependencies, package compiling and making distributable packages. After installing Rust, restart your system. Otherwise, you might get command errors while running the cargo commands.
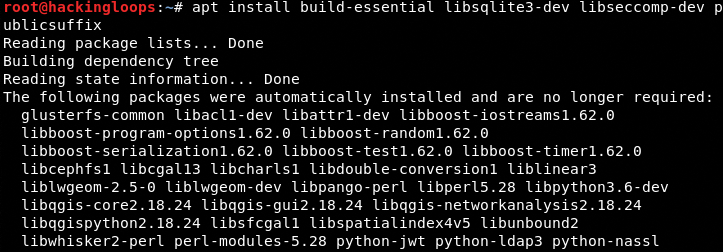
Install the following dependencies if they are not already installed on your system.
apt install build-essential libsqlite3-dev libseccomp-dev publicsuffix
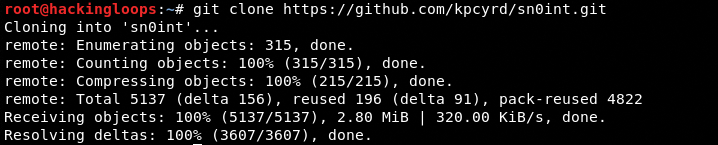
After installing the dependencies, clone Sn0int from Github using the following command.
git clone https://github.com/kpcyrd/sn0int.git
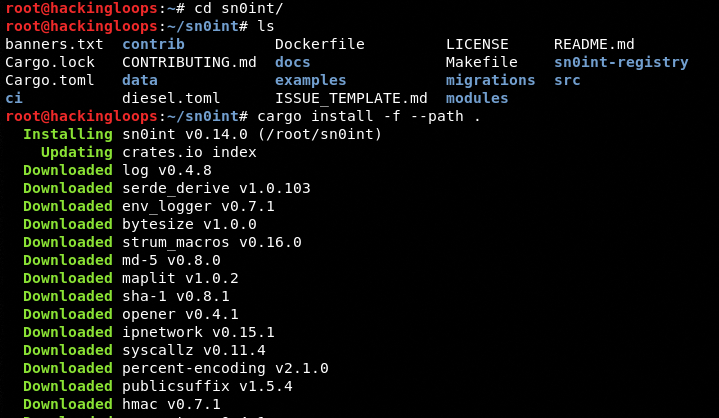
Navigate to the sn0int directory and run the following cargo path command to complete the installation.
cd sn0int
cargo install -f --path .
First Interaction with Sn0int
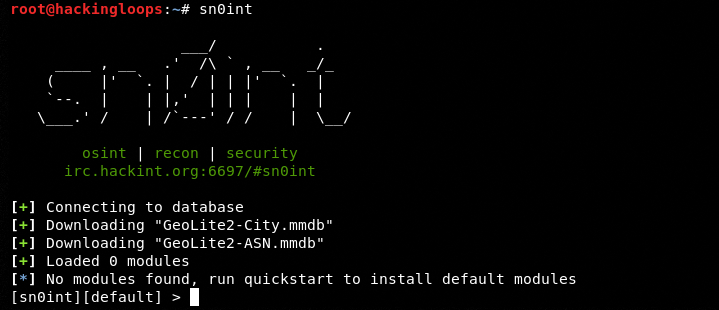
Sn0int installs the default modules during the first run of the framework. The following command executes Sn0int in the terminal.
sn0int
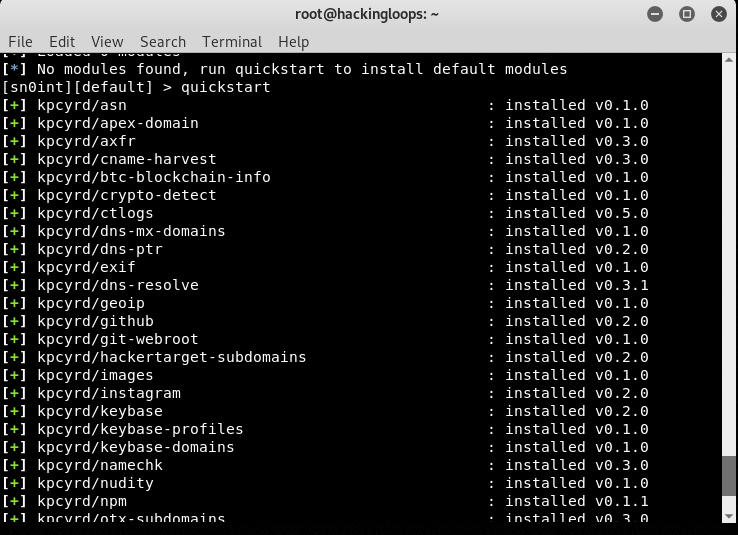
As we can see in the screenshot, Sn0int comes with no pre-installed modules. Running the quickstart command installs all the default modules of the framework.
quickstart
The –help command shows different types of command arguments we can use to perform the intelligence tasks.
–help
There is a subcommand help section showing different arguments that can be used while running specific modules.
Creating Workspace
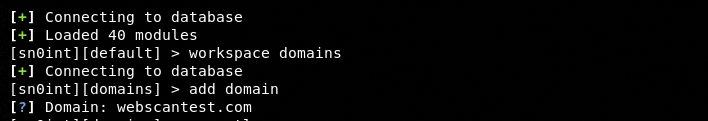
We can create different workspaces in Sn0int for different intelligence projects. Let’s create an example workspace called domains using the following command.
workspace domains
We can add the target domain to the workspace as follows.
add domain
Domain: webscantest.com
Running Modules
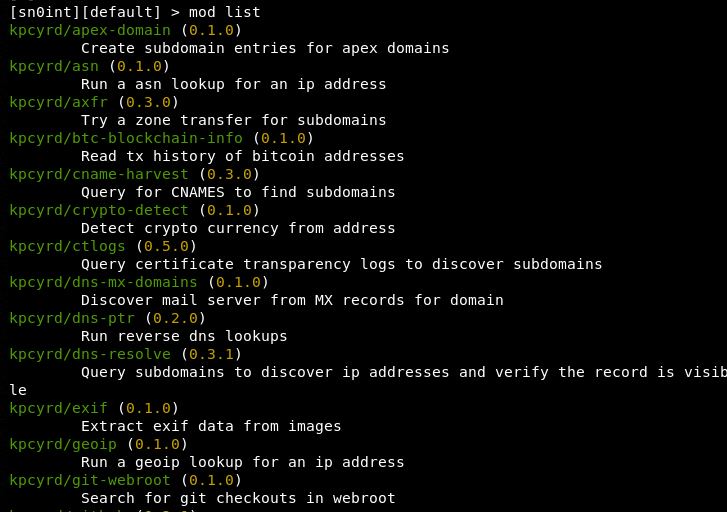
The mod list command lists all the installed modules. Currently, there are 40 default modules available in Sn0int.
mod list
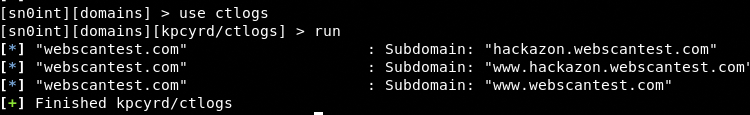
We can call any module through the use command. Let’s call the certificate transparency logs (ctlogs) module to find the subdomains associated with the target domain (webscantest.com).
use ctlogs
run
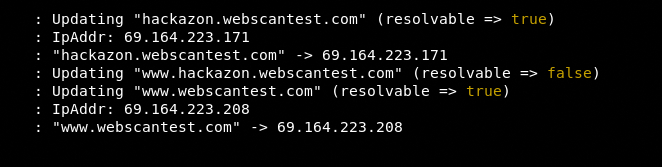
As we can see the framework has found few subdomains associated with the target domain. The dns-resolve module can find out which subdomains (hosts) are resolvable and their IP addresses.
use dns-resolve
run
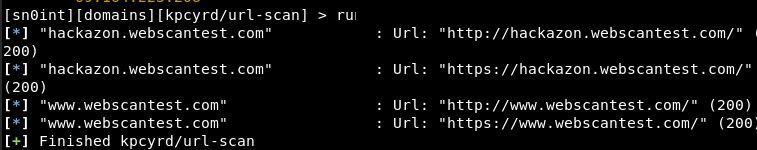
The next module we can try is url-scan that identifies the webpages on each host.
use url-scan
run
The above results not only validate the existence of web pages for each subdomain but also confirm the open status of port 80 and 443 for each target host. The results also show the http and https responses by the target hosts. We can apply more modules to further investigate the target as per the requirements.
Conclusion
Sn0int can perform open-source intelligence tasks in sequential orders. We can generate a hierarchy of information and store results in a database.





Comentários
Postar um comentário