Configuration
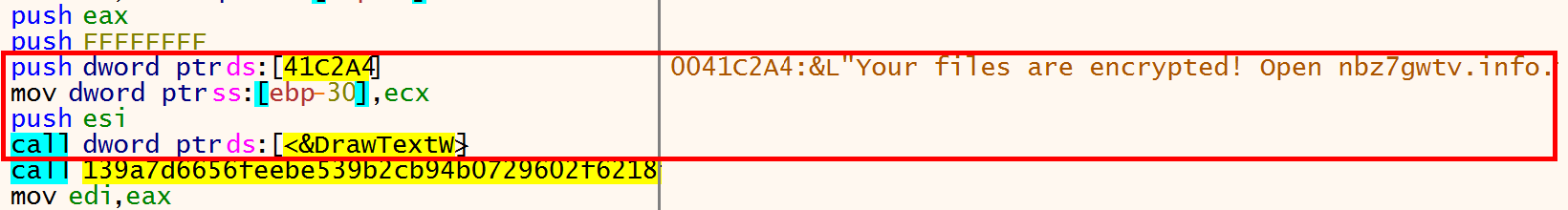
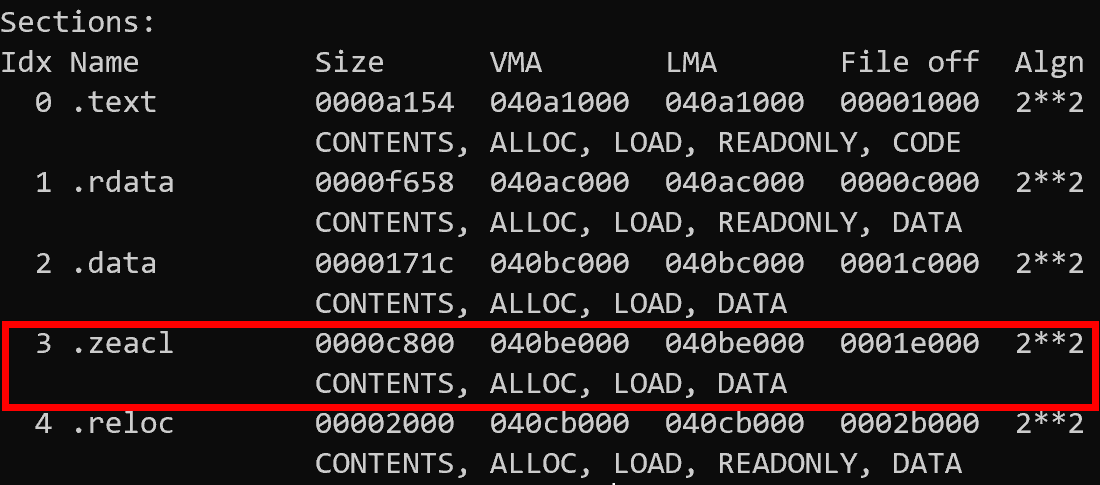
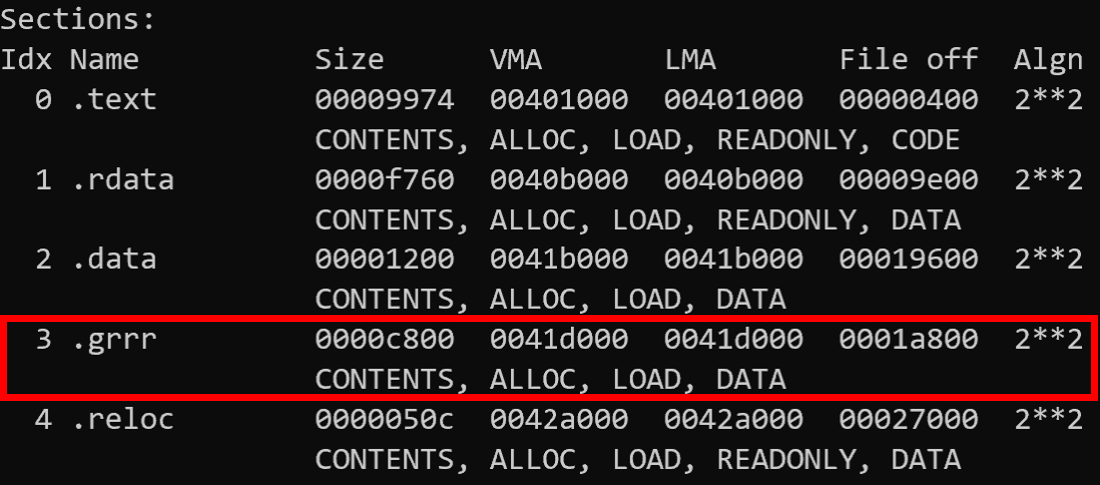
To enable threat actors to customize their Sodin campaign, the family includes a configuration file embedded within the executable. This is packaged as a PE section with a distinct name - the 2 variants we have examined for this blogpost used .grrr and .zeacl.
PE sections from unpacked Sodin samples
These sections are a JSON configuration file encrypted using RC4 which contain a large amount of information about the particular campaign the sample belongs to
{
"pk": "GadtWz2QBTacskL+55Wpo65IkwY28qJOxHoe4Xte81M=",
"pid": "10",
"sub": "7",
"dbg": false,
"fast": true,
"wipe": true,
"wht": {
"fld": ["appdata", "google", "msocache", "mozilla", "program files", "windows", "perflogs", "application data", "windows.old", "system volume information", "program files (x86)", "$windows.~ws", "intel", "$recycle.bin", "$windows.~bt", "programdata", "boot", "tor browser"],
"fls": ["ntuser.dat.log", "bootsect.bak", "ntuser.dat", "iconcache.db", "ntldr", "autorun.inf", "boot.ini", "bootfont.bin", "desktop.ini", "thumbs.db", "ntuser.ini"],
"ext": ["ldf", "msi", "nomedia", "msu", "wpx", "ani", "shs", "theme", "386", "adv", "icns", "lnk", "ico", "ics", "rom", "sys", "mod", "cur", "com", "scr", "cpl", "diagcfg", "lock", "diagcab", "msstyles", "idx", "msc", "icl", "rtp", "exe", "drv", "hta", "nls", "deskthemepack", "cmd", "hlp", "themepack", "dll", "mpa", "msp", "ps1", "prf", "ocx", "bat", "diagpkg", "cab", "bin", "spl", "key"]
},
"wfld": ["backup"],
"prc": ["mysql.exe"],
"dmn": "lyricalduniya.com;theboardroomafrica.com;chris-anne.com;ownidentity.com;web865.com;[...]",
"net":true,
"nbody ":"SABlAGwAbABvACAAZABlAGEAcgAgAGYAcgBpAGUAbgBkACEADQAKAA0ACgBZAG8AdQByACAAZgBpAGwAZQBzACAAYQByAGUAIABlAG4AYwByAHkAcAB0AGUAZAAsACAAYQBuAGQALAAgAGEAcwAgAHIAZQBzAHUAbAB0ACAAeQBvAHUAIABjAGEAbgAnAHQAIAB1AHMAZQAgAGkAdAAuACAAWQBvAHUAIABtAHUAcwB0ACAAdgBpAHMAaQB0ACAAbwB1AHIAIABwAGEAZwBlACAAdABvACAAZwBlAHQAIABpAG4AcwB0AHIAdQBjAHQAaQBvAG4AcwAgAGEAYgBvAHUAdAAgAGQAZQBjAHIAeQBwAHQAaQBvAG4AIABwAHIAbwBjAGUAcwBzAC4ADQAKAEEAbABsACAAZQBuAGMAcgB5AHAAdABlAGQAIABmAGkAbABlAHMAIABoAGEAdgBlACAAZwBvAHQAIAB7AEUAWABUAH0AIABlAHgAdABlAG4AcwBpAG8AbgAuAA0ACgANAAoASQBuAHMAdAByAHUAYwB0AGkAbwBuAHMAIABpAG4AdABvACAAdABoAGUAIABUAE8AUgAgAG4AZQB0AHcAbwByAGsADQAKAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQANAAoASQBuAHMAdABhAGwAbAAgAFQATwBSACAAYgByAG8AdwBzAGUAcgAgAGYAcgBvAG0AIABoAHQAdABwAHMAOgAvAC8AdABvAHIAcAByAG8AagBlAGMAdAAuAG8AcgBnAC8ADQAKAFYAaQBzAGkAdAAgAHQAaABlACAAZgBvAGwAbABvAHcAaQBuAGcAIABsAGkAbgBrADoAIABoAHQAdABwADoALwAvAGEAcABsAGUAYgB6AHUANAA3AHcAZwBhAHoAYQBwAGQAcQBrAHMANgB2AHIAYwB2ADYAegBjAG4AagBwAHAAawBiAHgAYgByADYAdwBrAGUAdABmADUANgBuAGYANgBhAHEAMgBuAG0AeQBvAHkAZAAuAG8AbgBpAG8AbgAvAHsAVQBJAEQAfQANAAoADQAKAEkAbgBzAHQAcgB1AGMAdABpAG8AbgBzACAAaQBuAHQAbwAgAFcAVwBXACAAKABUAGgAZQAgAGYAbwBsAGwAbwB3AGkAbgBnACAAbABpAG4AawAgAGMAYQBuACAAbgBvAHQAIABiAGUAIABpAG4AIAB3AG8AcgBrACAAcwB0AGEAdABlACwAIABpAGYAIAB0AHIAdQBlACwAIAB1AHMAZQAgAFQATwBSACAAYQBiAG8AdgBlACkAOgANAAoALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAC0ALQAtAA0ACgBWAGkAcwBpAHQAIAB0AGgAZQAgAGYAbwBsAGwAbwB3AGkAbgBnACAAbABpAG4AawA6ACAAaAB0AHQAcAA6AC8ALwBkAGUAYwByAHkAcAB0AG8AcgAuAHQAbwBwAC8AewBVAEkARAB9AA0ACgANAAoAUABhAGcAZQAgAHcAaQBsAGwAIABhAHMAawAgAHkAbwB1ACAAZgBvAHIAIAB0AGgAZQAgAGsAZQB5ACwAIABoAGUAcgBlACAAaQB0ACAAaQBzADoADQAKAHsASwBFAFkAfQAAAA==",
"nname": {"EXT"}.info.txt,
"exp":false,
"img":"WQBvAHUAcgAgAGYAaQBsAGUAcwAgAGEAcgBlACAAZQBuAGMAcgB5AHAAdABlAGQAIQAgAE8AcABlAG4AIAB7AEUAWABUAH0ALgBpAG4AZgBvAC4AdAB4AHQAIQAAAA=="
}
There are quite a few useful fields in here - these are outlined in the table below.
| Field Name | Description |
| pk | Base64-encoded public key used for file encryption |
| pid | Only used if net field is also set, sent to C2 servers. Likely related to campaign identifier etc. |
| sub | See pid |
| dbg | Enable/disable debug mode (for the malware author) |
| fast | Boolean value which changes how large files are encrypted |
| wipe | Boolean. If set, sample will try to erase contents of folders blacklisted in the wfld field |
| wht |
Defines whitelists for encryption process. Contains 3 sections:
- fld: folders to ignore
- fls: specific files to ignore
- ext: whitelisted file extensions
|
| wfld | List of folder names. If the wipe field is set to true then the malware will attempt to erase the contents of all folders listed here |
| prc | List of process names the malware will try to terminate before carrying out file encryption |
| dmn | List of domain names which the malware will attempt to contact to use as C2 |
| net | Boolean value. Sets whether sample should send host information to C2 servers listed in dmn key |
| nbody | Base64-encoded version of the ransom note dropped to the file system after encryption |
| nname | Filename of the ransom note |
| exp | Boolean value. Defines whether or not the malware will use an exploit to try and escalate privileges on the system |
| img | Base64-encoded version of the text shown in the wallpaper background set by the malware. |
Configuration field details
When delivered to a new system Sodin samples are packed using a custom algorithm, hiding the existence of the specially named resource sections. The malware uses a PE overwrite approach to its unpacking mechanism - it allocates heap space using LocalAlloc, writes the unpacker stub to it, and then passes execution to that area after marking it RWX with VirtualProtect.
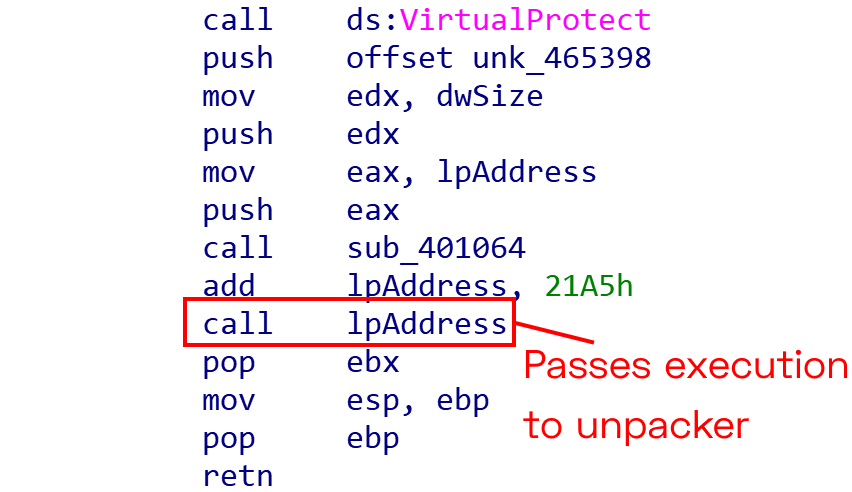
Create and call unpacker stub
The unpacker stub then writes the new PE to the address space in which the original file was mapped, clearing the content of the entire region before writing the new executable and jumping back to the updated Entry Point. We can now dump the executable and examine the sections, as shown previously.
The configuration itself is still encrypted at this stage, but in its unpacked form it is possible to analyze the decryption process and recreate it. The algorithm is RC4 - we can clearly see the SBox creation and swapping operations - but some minor changes have been made to prevent easy decryption with standard RC4 tools.
Examining the executable we can see that the key for the decryption is the first 32 bytes of the resource section.
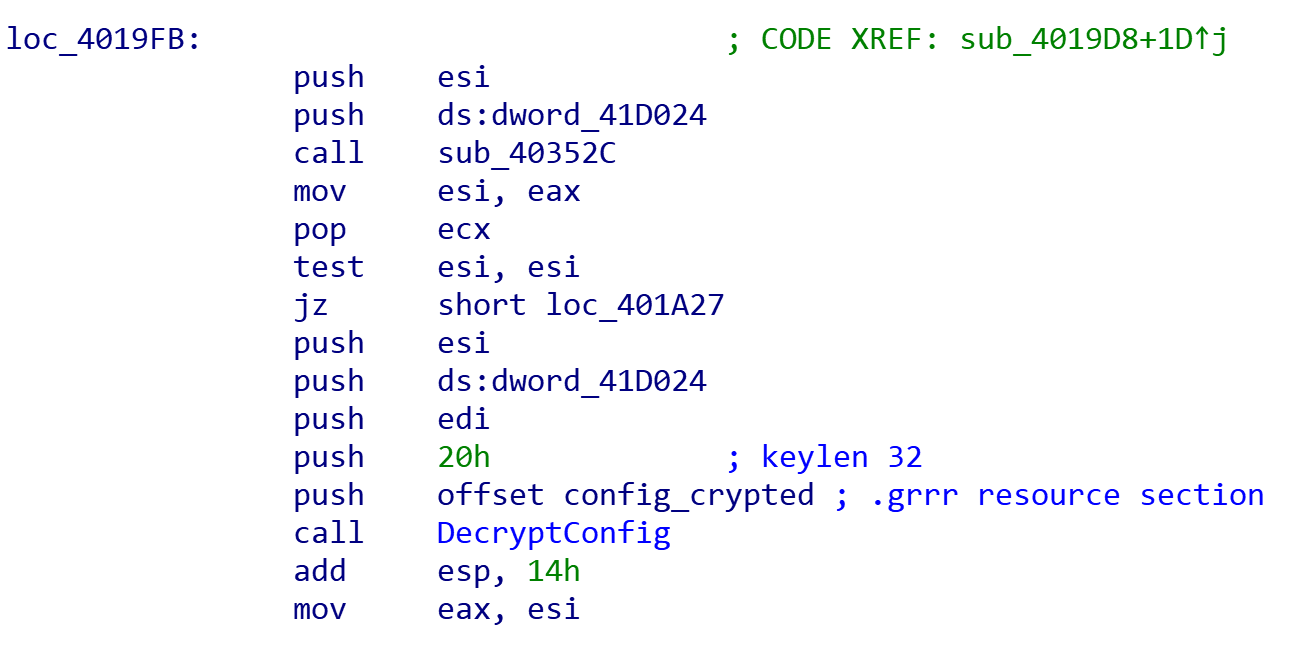
Preparing keylength and ciphertext parameters and passing them to the configuration decryption function
With this information and analysis of the decryption function, it was possible to build a configuration extractor to parse and report details from these configurations during dynamic analysis of the samples. In Hatching Triage, we have implemented a system that enables taking process memory dumps when particular conditions are met during an analysis. Using this, we can obtain the unpacked executable and run processing on it to include the information in the analysis report and enable easy identification of particular campaigns or actors.
The Sodin extractor is not available on Triage yet while testing and improvements to the memory dumping methodology are implemented, but keep an eye on our
Twitter account for updates when that is released.
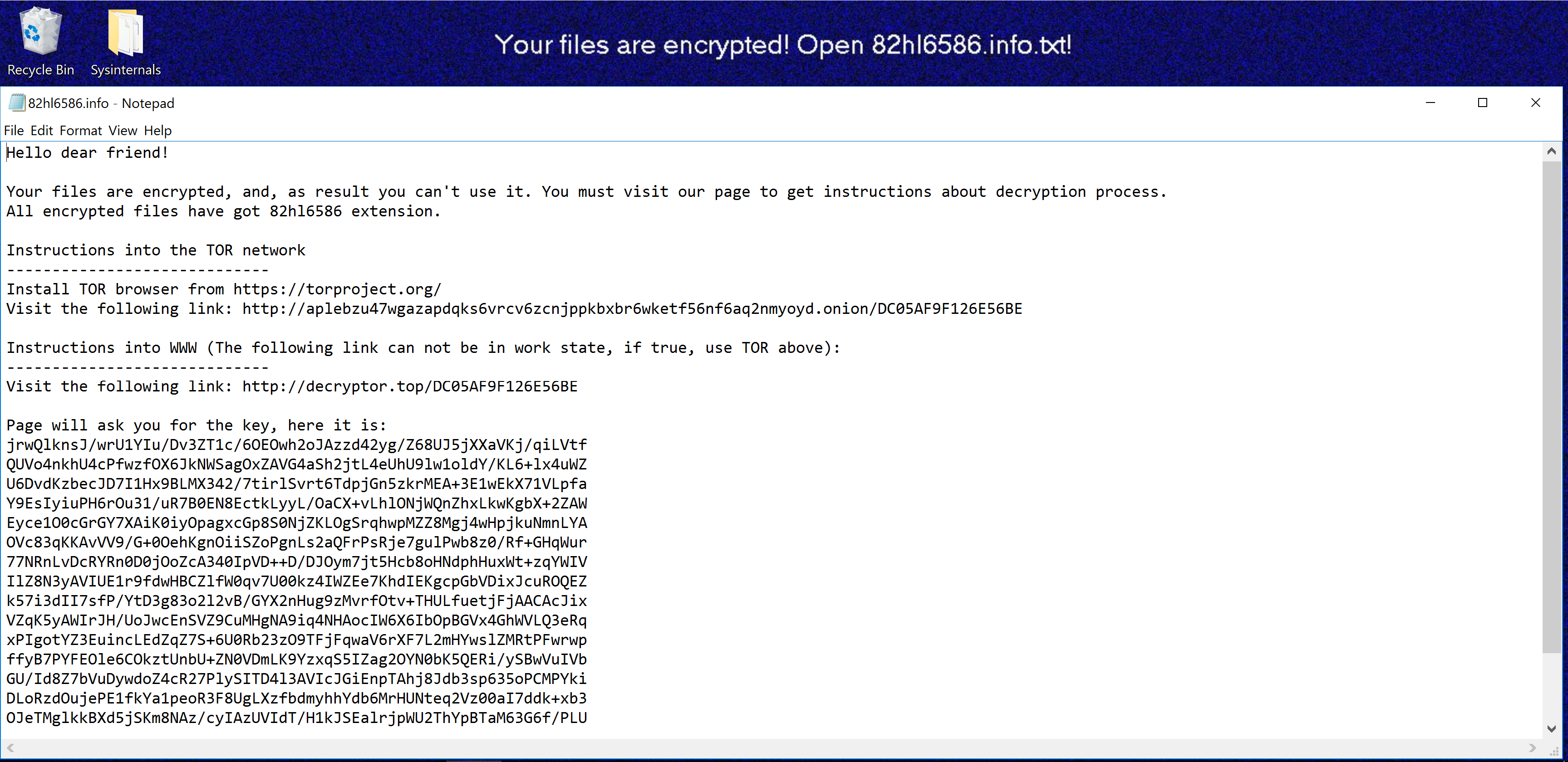
File Encryption
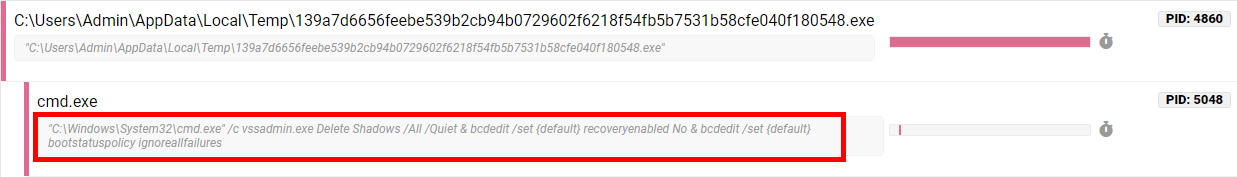
Sodin can encrypt files on local storage or any mapped network shares, overwriting the original files and renaming them with an extension generated on a per-infection basis. This process is highly customizable through the embedded configuration section, allowing for certain files/folders to be whitelisted and protected from the encryption process. The Sodin executable also accepts a command-line parameter - by passing the value -nolan, one can disable the encryption of mapped network shares and limit the effects to only the infected machine.
"wht": {
"fld": ["appdata", "google", "msocache", "mozilla", "program files", "windows", "perflogs", "application data", "windows.old", "system volume information", "program files (x86)", "$windows.~ws", "intel", "$recycle.bin", "$windows.~bt", "programdata", "boot", "tor browser"],
"fls": ["ntuser.dat.log", "bootsect.bak", "ntuser.dat", "iconcache.db", "ntldr", "autorun.inf", "boot.ini", "bootfont.bin", "desktop.ini", "thumbs.db", "ntuser.ini"],
"ext": ["ldf", "msi", "nomedia", "msu", "wpx", "ani", "shs", "theme", "386", "adv", "icns", "lnk", "ico", "ics", "rom", "sys", "mod", "cur", "com", "scr", "cpl", "diagcfg", "lock", "diagcab", "msstyles", "idx", "msc", "icl", "rtp", "exe", "drv", "hta", "nls", "deskthemepack", "cmd", "hlp", "themepack", "dll", "mpa", "msp", "ps1", "prf", "ocx", "bat", "diagpkg", "cab", "bin", "spl", "key"]
}
Whitelist configuration section
The keys specify whitelists for:
- fld - folder names
- fls - specific file names
- ext - file extensions
The malware iterates through every directory and file on the system, checking them against these configuration values and queuing them up for encryption if they are not excluded. Once encrypted, the files are renamed with a new extension.
Encrypted File Extension
Before starting the encryption process, Sodin generates the random file extension which is applied to every encrypted file. The extension is a string of letters and numbers from 5 to 10 characters long, which is generated and saved to the registry along with other information gathered at various stages (discussed below).
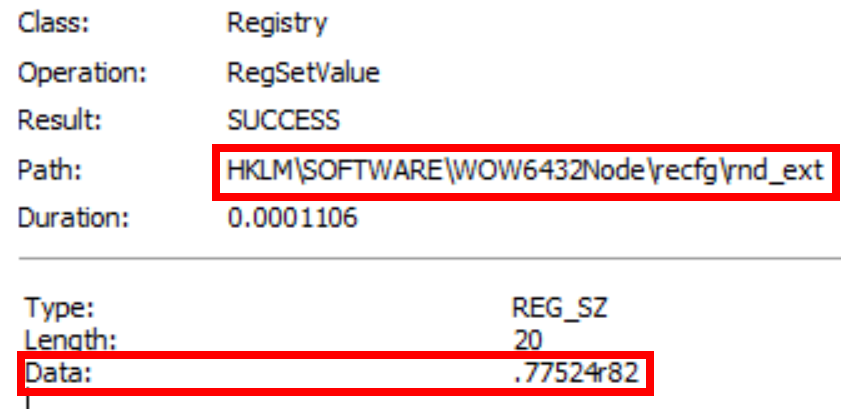
File extension saved to SOFTWARE\WOW6432Node\recfg\rnd_ext
The extension itself is tricky to accurately identify as Sodin-related due to the generic nature of it, but the registry path is relatively specific and is readily detectable in a sandbox.
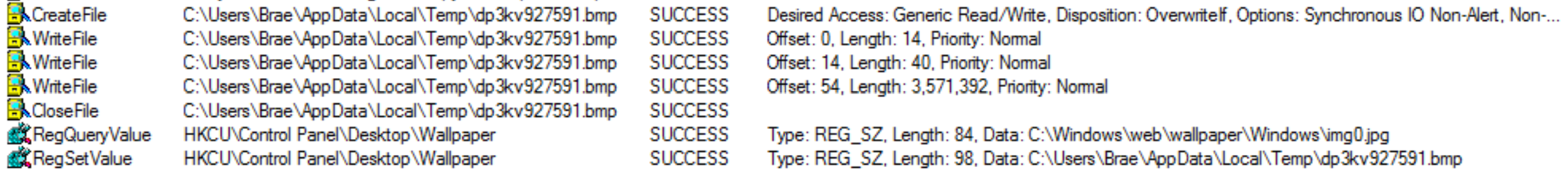
Other Registry Changes
As well as the file extension, Sodin saves a few other bits of data to the Software\Wow6432Node\recfg registry key.
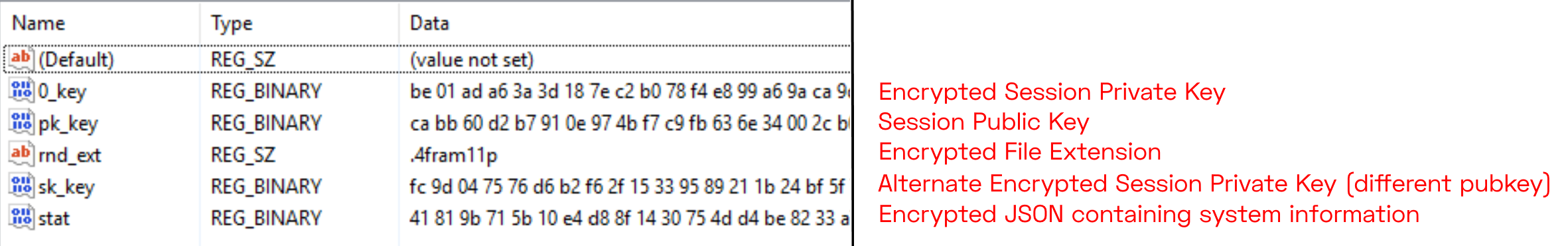
Values within the recfg registry key
None of the values assigned to these keys are static, but all of the key names are common across Sodin samples. We won't go into the details of these here, but the image above gives a basic outline of the contents.
In a dynamic environment, this sort of registry structure is ideal for identifying a family.
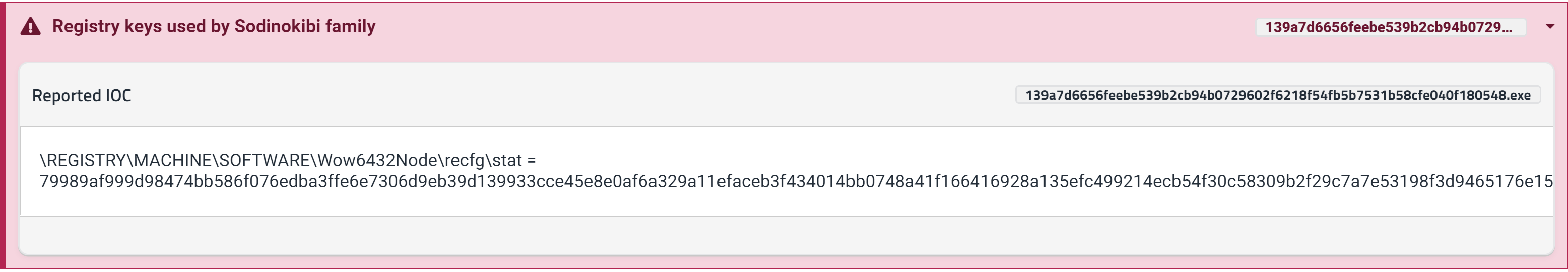
Tria.ge signature output for registry keys









Comentários
Postar um comentário