The Ultimate OSINT Guide — Learn How Information Is Found Online OSINT (Open Source Intelligence) is one of the most powerful techniques used in cybersecurity, investigations, and digital intelligence. Security researchers, analysts, and investigators use publicly available data to gather insights, detect threats, and uncover hidden connections across the internet. In this guide you’ll discover how OSINT can be used for: Digital investigations Online footprint analysis Intelligence gathering from public sources Security research & threat analysis OSINT proves that information is everywhere — if you know where to look. For educational & cybersecurity awareness purposes only. Comment OSINT and check the pinned post on my page for the full guide. Don’t forget to save this post for later. Olá INTERNAUTA, #osint Você está procurando maneiras de economizar dinheiro, melhorar a segurança e aumentar a produtividade de sua empresa? Se sim, você deve considerar usar fontes aberta...
Compartilhe
- Gerar link
- X
- Outros aplicativos
Tracing an offshore bank and a dark web service using the blockchain
Tracing an offshore bank and a dark web service using the blockchain — an OSINT investigation
Cryptocurrency crimes and scams are inevitable, and there’s no place better than the dark web with the added anonymity.
However, not only is it easy to identify the relationship between certain sites, but there are also a number of ‘digital fingerprints’ an onion site can leave behind.
In this case study, we take a look at:
- How to identify the link between onion sites (the dark web)
- How to identify the relationship between two bitcoin addresses
- How to trace addresses to a registered exchange
For a visual explanation, this is what we are going to look at:
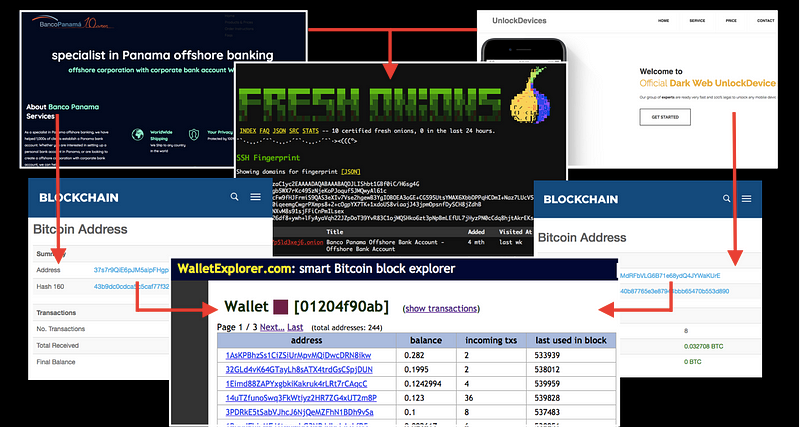
The Dark Web Services —Two Of The Many
The two subjects of this case study are BancoPanama, a banking site selling anonymous ‘offshore banking accounts’ for bitcoin, and Dark Web UnlockDevices, a service that allows you to anonymously unlock phones through bitcoin payment.
This case study is not to identify whether these are scam sites or not. Rather, it is to identify the relationship between them, to show that they are owned by the same person, and to trace their blockchain fingerprints to a registered cryptocurrency exchange.
Analysis Tools For Dark Web Onion Sites
In this case study, we are going to use four tools, they are:
- Fresh Onions (http://zlal32teyptf4tvi.onion/)
- Wallet Explorer (https://www.walletexplorer.com/)
- Blockchain Explorer (https://www.blockchain.com/explorer)
- Tor Browser (https://www.torproject.org/)
The most important of these two tools are Fresh Onions and Wallet Explorer.
Fresh Onions is a crawler for websites. It basically tells you any hidden information that you might not see on an onion site and is great for identifying any of these ‘digital fingerprints’ we are looking for.
Wallet Explorer is useful as it identifies all Bitcoin addresses owned by one single wallet. When dealing with cryptocurrencies, one wallet may own numerous addresses.
The Blockchain Explorer and Tor browser are platforms you will already be familiar with. You will need Tor to open any of the onion links I have provided here.
Identifying ‘Fingerprints’ Of Dark Web Services
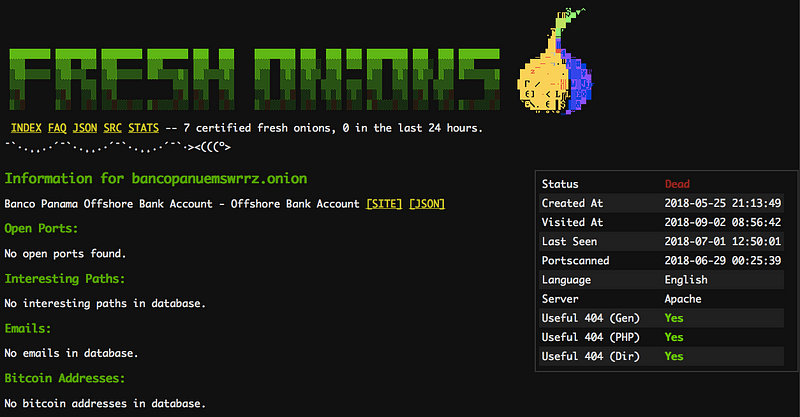
The relationship between these two dark web onion sites can identified using the Fresh Onion crawler.
The relevant details we are looking for is an ‘SSH Fingerprint’. Essentially it is a unique marker a site will carry. With Fresh Onions, we can see all of the other sites that hold that same fingerprint.
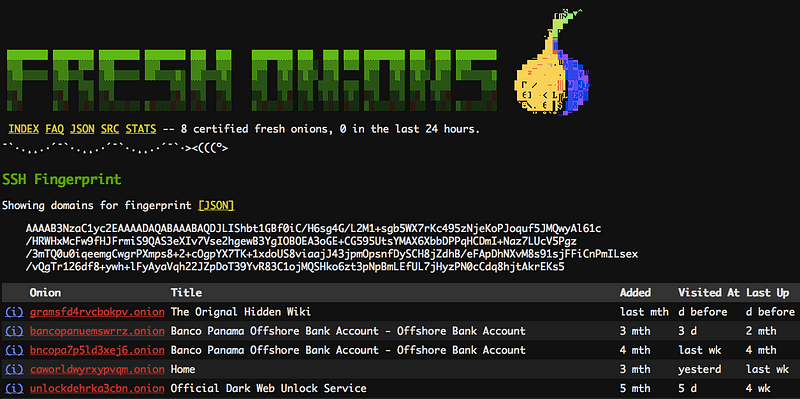
This shows that there is a SSH relationship between the two onion sites we identified earlier.
Now let’s take a look at the blockchain evidence.
How To Use Blockchain Forensics On Transactions
The first step to any analysis of a dark web site is to locate its cryptocurrency address.
This may be various currencies, but for the most part, bitcoin is the ruler of the crypto world, and thankfully it has a very public blockchain.
We can tell a number of things just from one bitcoin address, such as:
- How many transactions have taken place
- Where money has come from and how much
- Where money has been sent and how much
- A historical timeline of transactions
- And other associated bitcoin addresses in that wallet
The last one of these is where the site Wallet Explorer comes into effect.
With this tool, we are able to identify any other bitcoin addresses owned by the same wallet.
So what’s the relationship between the two sites I mentioned?
When we access their bitcoin addresses through the ‘purchase’ section of the website, we can identify two main addresses:
The relationship between these two websites is that they are from the same wallet, meaning that they are owned by the same entity or person.
I found this using Wallet Explorer, where we can identify the dual ownership of the addresses by simply entering one into the search function, and then revealing the entire wallet. Using a simple ‘CNTRL F’ reveals both are present.
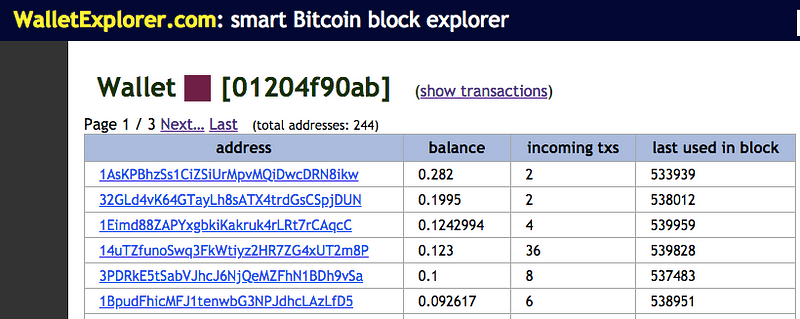
Now let’s take a look at the specific transactions of each of these bitcoin addresses.
Tracing the payments through to an exchange
The transactions paid into these accounts are what normal transactions should look like when viewed on the blockchain.
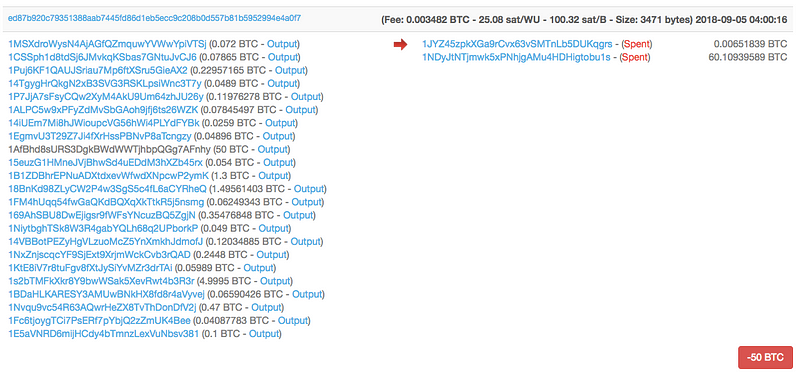
For instance, in the transaction below we see money shifted from one bitcoin address to the Dark Web UnlockDevices address ending in KUrE:
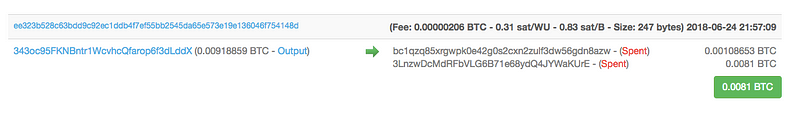
But following the outgoing transactions use more addresses:
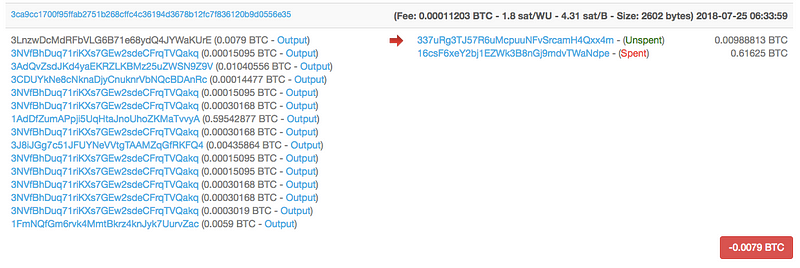
As you can see in the screenshot above, there are a number of addresses included in the same exchange.
- A bitcoin mixing service, or
- An exchange
For many vendors on the dark web, a mixing service, or cryptocurrency tumbler, guarantees anonymity as it essentially scrambles the addresses and the payments made — perfect for illegal vendors and scammers, not for law enforcement.
Ndpe is a unique address as the majority of its payments are made intobitcoin address 1NDyJtNTjmwk5xPNhjgAMu4HDHigtobu1s.
You can see this in the screenshots below:
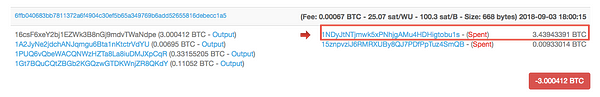
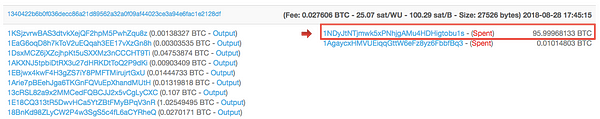
We can see this through a simple Google search, which also reveals the following Tweet from Binance themselves.
Blockchain Analysis of the Ndpe Address
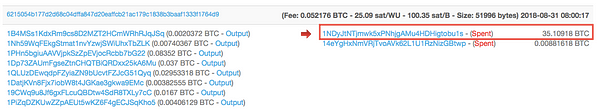
As you can see in the screenshot below, this wallet contains more than 120,000 bitcoin addresses, many of which are seeing large volumes of transactions every day.
Ndpe is likely the bitcoin address of an exchange, or it may be a very well-used bitcoin tumbling service, which would explain the large volume of bitcoin addresses it holds in its wallet, allowing it to essentially scramble transactions.
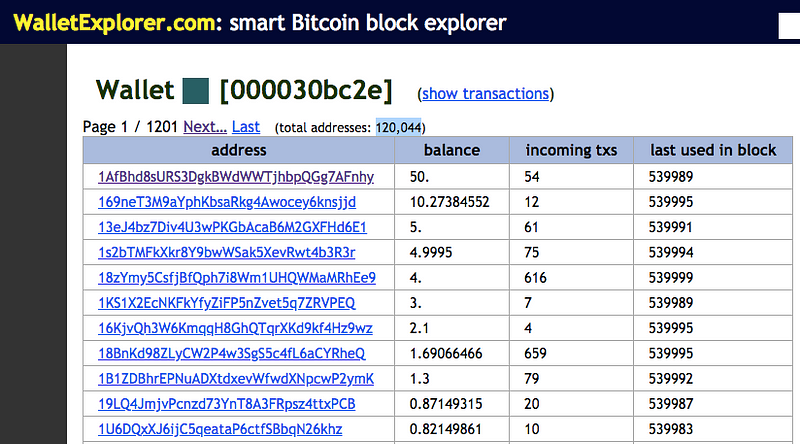
Each one of the addresses in this wallet use Binance as the final source of all of their transactions.
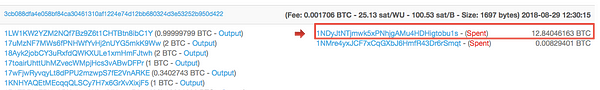
In the above screenshot, the top five addresses all show their largest payouts to Binance. We can see this on the blockchain.
Here is a recent outgoing transaction to Binance from Fnhy:
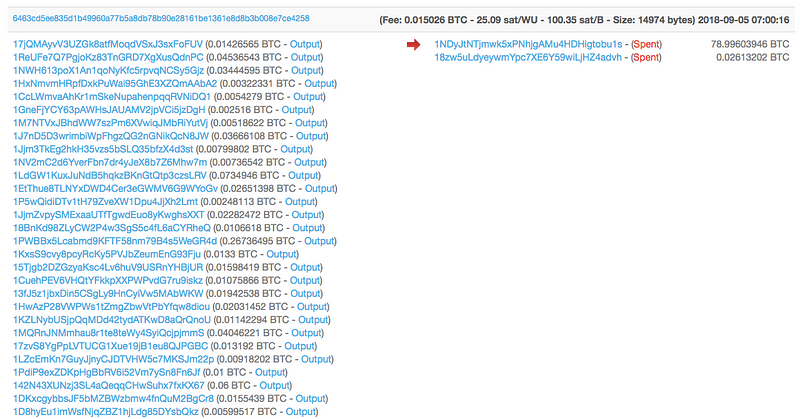
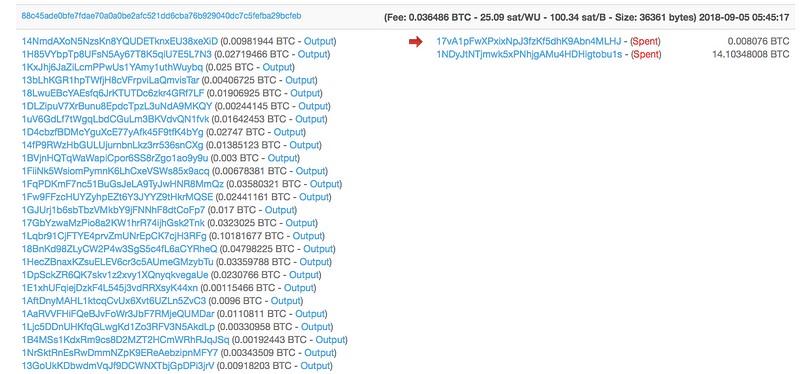
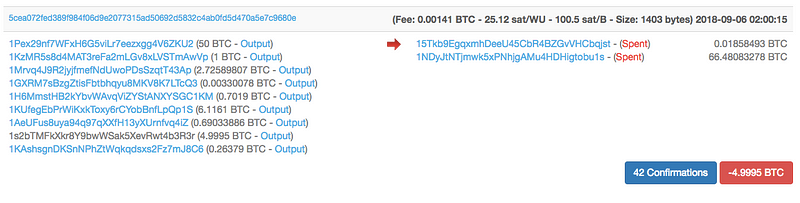
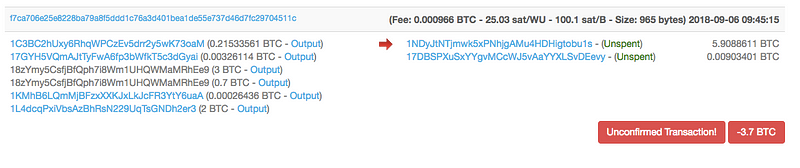
As you can see, there is a relationship of funds from these two dark web onion sites, to the Ndpe address on the blockchain.
Since we have established that these two dark web onion sites are ran by the same owner, it is likely the person is using a single tumbler or exchange.
There is also an ongoing financial relationship between the Ndpe address, and other addresses in the same wallet, and Binance’s address ending in bu1s.
Where open-source methods stop
Using open-source information on the dark web and the blockchain only gets you so far.
Once we have hit this point, it is now up to relevant parties, as well as a cryptocurrency exchange’s own housekeeping to find the registration details of any accounts associated with illegal activity on the dark web.
- Gerar link
- X
- Outros aplicativos
Postagens mais visitadas
🇧🇷 Ferramentas OSINT mais usadas por policiais no Brasil
- Gerar link
- X
- Outros aplicativos
Comandos Google Dorks
- Gerar link
- X
- Outros aplicativos
Ferramentas de pesquisa
- Gerar link
- X
- Outros aplicativos
Gmail OSINT: Como investigar contas do Gmail com ferramentas OSINT
- Gerar link
- X
- Outros aplicativos
Top 10 Popular Open Source Intelligence (OSINT) Tools
- Gerar link
- X
- Outros aplicativos





Comentários
Postar um comentário