Compartilhe
- Gerar link
- X
- Outros aplicativos
GPU Password Cracking – Bruteforceing a Windows Password Using a Graphic Card
GPU Password Cracking – Bruteforceing a Windows Password Using a Graphic Card
GPGPU computing is getting lots of attention these days. GPGPU computing simply means doing general calculations on graphic cards (GPUs) rather than CPUs. Traditionally, GPUs were used only for getting graphical output, rendering frames in games and other purposes related to graphics. Lately, people started realizing that GPUs are far more efficient at handling highly parallel tasks and that there should be a way to code for graphic cards. Though GPGPU computing is still at its infancy, a lot of progress has been made toward this direction. For example GPUs are used to speed up video conversion, video processing, doing scientific calculations, folding and password hash cracking.
The last one – password cracking looks very interesting and we are going to discuss about just that. Recently I came across a free password hash cracker called ighashgpu. This tool is developed by a guy called Ivan Golubev. It’s a command-line utility meaning, there is no GUI. Though allergic to command-line utilities, curiosity made me to meddle with the tool to see how fast my Radeon 5770 would crack passwords and the results are simply amazing.
The tool supports these hashes;
- Plain MD4, MD5, SHA1.
- NTLM
- Domain Cached Credentials
- Oracle 11g
- MySQL5
- MSSQL
- vBulletin
- Invision Power Board
- and more …
Cracking an NTLM Password Hash with a GPU
I’m going to use the NTLM hash here. If you are wondering what NTLM is, your Windows (NT and above) logon passwords are not stored as plain text but encrypted as LM and NTLM hashes. They are not reversible and hence supposed to be secure. LM hashes can easily be broken using Rainbow Tables but NTLM hashes are relatively stronger. But that’s not stopping us from cracking them.
For comparison, I’m going to use another popular and free security tool – Cain & Abel. This is an excellent tool for breaking different passwords, using the CPU.
To crack a password, you need to have the NTLM hash of that password. Fortunately, Cain & Abel has a hash calculator. So let’s do some password cracking.
A password with 5 characters
Using Cain, I generate a random password “fjR8n” whose NTLM hash is “AA8251D1BB587ABFAE6403194216041F” without quotes of course.
Now that the password has upper, lower case letters and a number. So the character set should be like this in Cain to crack the password.
As you see, Cain has taken about 24 seconds to crack the password at the rate of 9.8 million passwords/sec.
Let’s see what ighashgpu has to offer.
The password is found in less than one second. Secondly look at how many passwords the GPU has churned out per second. Dude, it’s 3.334 billion passwords.
A password with 6 characters
Let’s now take “pYDbL6” as the 6 character password. The NTLM hash for that password is CB898E9CA230D14413756875DD8BF71D.
Now that Cain reports it would take approximately 1 hour and 30 minutes to crack our password. Note that this is the maximum time Cain would take to crack the password. It could even be less than that, depending on the password.
What about ighashgpu?
Ighashgpu finds the password in staggering 4 seconds. Also note that the maximum time it would take to crack a 6 character alphanumeric password is about 17 seconds. See the difference between GPU and CPU computing?
A 7 character password
Let’s take “fh0GH5h” as the 7 character password whose NTLM hash is 29152D8B2EB5806302EB5829635309E6.
Cain would take about 4 days to crack the 7 character alphanumeric password.
But ighashgpu would take about just 17 minutes and 30 seconds maximum to crack the password hash. Also note that the password is already found in 2 minutes and 15 seconds. This means, my GPU would only take 17 minutes and 30 seconds max to crack ANY 7 character alphanumeric password.
An 8 character password
Let’s make things more interesting now. I take “t6Hnf9fL” as the 8 character alphanumeric password whose NT hash is 7B0E126699A3EE5F0108D07926448E47
Aargh, Cain would take almost one year to crack that password.
What about ighashgpu?
Isn’t it astonishing? Ighashgpu can crack this hash in 18 hours and 30 minutes.
Okay, let’s give some challenge to my GPU.
A 9 character password
Our candidate here is “kfU64FdB8” – 75A7AF26871E71BCF853509C47DB3475
Err, you have to wait for more than 43 years before you find the password if you use Cain.
Let’s move on to ighashgpu.
Isn’t 48 days better than 43 years?
Okay guys, we just saw that a Radeon 5770 GPU would take 48 days to break a 9 character password. My tests also revealed that a 5770 would take 8 years and 70 days to break a 10 character alphanumeric password. Now it’s time to add special characters to the mix.
First thing first. Our 7 character mixed symbols password and it’s hash “F6&B ls” (note the space) – B438599AC14AB16E2F889A4471F7C76F
Cain will take 75 days.
Ighashgpu wouldn’t even take 7 hours to finish the job.
What about an 8 character password?
While Cain would take more than 19 years, ighashgpu can crack the password within 26 days. Far better.
Okay guys, we have just seen what ighashgpu can do for us. It’s fast, really fast indeed for password cracking, since it uses GPU. It can crack any simple and short password and even a simple 10 character password within acceptable time limits. With GPUs becoming more and more powerful, things are only going to get worse. So what length is safe? Can we say a 12 character password is safer? Maybe, but chances are there that we may choose mixture of common words (like names and numbers) as long passwords which may be easily broken with a simple dictionary attack.
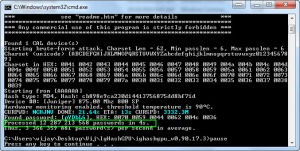
If your password contains just numbers, even if it’s 10 characters in length, it can easily be broken with ighashgpu. Let’s take a random 10 character numeric password – “8457317452” whose NT hash is 1089F7DE94ABEE2F38BFBA428C782905.
Look at the image. It’s horrible to know that this password is broken in less than two seconds!
Now I’m running out of patience to know how long my GPU would take to crack mixed (all symbols found on an US English keyboard) 8 character password.
Password: g&4K 3gI
Hash: 02944DC7857DFDDDE7DE6FDF38E9CC95
Just a little more than 25 days.
What about a 9 char password?
Password: H<k7$6fVJ
Hash: 4F5BBAB78A3551E369E205A3022920E9
Now it’s almost 7 years.
Got the drift? The more complex the password is, the longer the GPU will take to crack the password. So when you choose a password, make sure you don’t choose common words and names and always mix your password with letters, numbers and symbols.
We have just witnessed the power of a GPU against a CPU. GPUs are really fast and highly parallel. My Radeon 5770 is not the fastest card around but packs way more punch than a traditional CPU. It also looks like Radeon cards are faster than their Nvidia counterparts especially when it comes to password brute forcing and the latest Radeon 6990 graphic card should be several times faster than my Radeon 5770 and should make ANY 8 character password obsolete.
Have a look at my GPU in action.
Disclaimer:
As interesting as it may seem, password brute forcing can also be used for illegal purposes. I request you not to use the steps provided here for cracking others’ passwords and I take no responsibility for that.
Postagens mais visitadas
Ferramentas de pesquisa
- Gerar link
- X
- Outros aplicativos
🇧🇷 Ferramentas OSINT mais usadas por policiais no Brasil
- Gerar link
- X
- Outros aplicativos






















Comentários
Postar um comentário